Unicenter Asset Management
Asset Management
Components
- Asset Management consists of
components that manage, control, collect, process, maintain, and hold the
data used by the Asset Management system. The major components are:
- Admin Console - Management interface for scheduling requests and
actions, making queries, establishing policies, and more. The Admin
Console is the graphical user interface (GUI) for the Asset Management
System. The Admin Console can be run under Windows XP, Windows 2000, and
Windows NT and utilizes the Java Option (also known as W2), which can run
on multiple platforms, such as the Internet Explorer on NT or Netscape on
UNIX.
- Engine - Processor for distribution and collection of data.
The Engine performs data processing tasks on behalf of the Admin Console.
For example, the Engine can update the Domain Database with the status of
actions, or make queries against the Domain Database to find data. The
Engine runs as a service and is started automatically at startup time.
The Engine is generally scheduled to always run.
- Agent - Runs modules and scheduled jobs on target computers.
The Agent Software acts as a nonresident agent for the Admin Console,
performing the tasks that have been scheduled for either a computer or a
user from the Admin Console. The Agent can perform a variety of tasks,
from hardware and software inventory actions to running programs and
utilities for software maintenance and distribution.
- Domain (database) - Domain data repository for all units
(computers and users)
- Sector - Temporary storage area linking the Asset Management
Agent with the domain database
Asset Management
Installation
- The Asset Management
installation types can easily be executed using the wizard-like Asset
Management setup program. The Asset Management Product Explorer provides
the following types of software installation:
- Express Manager installation
- Express Agent installation
- Custom installation
- Add component
- Configure component
- Unattended Installation
- Installation with an Advantage
Ingres database
Admin Console
- The Enterprise Admin Console
lets you:
- View and manage data in the Enterprise database
and in domain databases
- Schedule actions to units and
groups at both the Enterprise
level and Domain levels
- From the Admin Console you can:
- Create and maintain computers
and users for configuration and scheduling purposes
- Define jobs for performing
actions on Agent computers
- Utilize modules for collecting
data from Agent computers
- Monitoring software packages
installed and started on Agent computers
- Manage sector settings and
properties
- Specify and execute queries
- Create and maintain policies
- Asset Management can modify all
files on all Agents, therefore a security system has been provided. Any
person wishing to start the Asset Management Admin Console must enter a
user name and password.
Unicenter Asset
Management Engine
- The Engine performs information
processing for the Admin Console. Information processing includes:
- Data collection
- Data distribution
- Job performance
- The Engine usually runs as a
Windows service on a dedicated Windows-based computer. However, it can
also run on the same computer running the Admin Console. Running the
Engine service on a dedicated computer will improve the response time of
the Admin Console when queries are made, and when Inventory updated from
many computers is processed.
- The tasks performed by the
Engine service include:
- Updating databases with
current information collected and provided by Asset Management agents
- Querying the databases for any
user-defined information on, for instance, computers or users
- Sending the query results to
the Admin Console
Units and Groups
- A Unit can be a computer, a
user, an engine, or any other type of equipment that you can define as a
new unit type, and is represented in the domain database. Each unit has a
name and area that identifies it. You can add new unit types or modify
existing unit types in the Asset Management system.
- For ease of configuration and
scheduling, it is convenient to define more than one unit as a collection
of units. This collection of units is called a Group. Asset Management is
easier to use when you have created groups that meet the precise demands
placed on your system.
Modules
- A module collects data from the
Agents. There are several different kinds of modules in Asset Management:
- Inventory Configuration - With the Inventory
Configuration module, you can define which hardware units from which you
want to collect information, from where, and at what level, such as per
user or group. An example of hardware you may want to monitor is the
processor.
- Template Configuration - With the Template
Configuration module, you can maintain your templates. Templates are used
to prompt end-users for information, usually about the computer or user,
and to add additional information types to the inventory system.
- Software Inventory - With the Software Configuration module, you
can define which file information is to be collected, from where, and at
what level, such as per user or group. Software inventory can also keep
track of your application licenses. An example of software you may want
to monitor is a word processing program. These modules can all be enabled
or disabled. When enabled, a module has a predefined setup. The setup can
be configured to suit your specific needs.
Jobs
- A Job is used to direct agents
or Engines to perform specific actions. You can, for example, use Jobs to
perform all software maintenance, including software distribution. You can
also schedule jobs to be executed on Agents.
- Jobs can be scheduled to
execute once, a specified number of times, or continuously. When you set
up a job, for example, you can schedule the action to execute in different
ways:
- Repeatedly
- At a specific date and time,
or after a period of time
- Based on day-of-the-week
dependencies
- Based on the execution of
another job, or the existence of a file, or an end-user decision to
execute the action now or later
Hardware Inventory
- Asset Management uses a
proprietary format and the DMI standard for collecting and updating the
Inventory information for a unit in the Asset Management database. Desktop
Management Interface (DMI) is a standard for managing the components of
hardware and logical devices. Components must provide a Management
Information Format (MIF) file to be DMI compliant.
- The Inventory module examines
computers connected to Asset Management on a scheduled basis. The module
uses a number of different sub-modules such as:
- Scanner for system hardware
information and information on hardware properties
- Scanner for specific network
information
- Agent for collection of MIF
files, generated by applications that are not part of Asset Management.
There are different modules for different operating systems.
- All information collected by
the Inventory module is stored in the domain database, and you can view it
from the Asset Management Admin Console.
Software Inventory
- You can use Asset Management
Software Inventory from the Admin Console to obtain information about the
software installed in your organization. The Software Inventory module can
detect software packages on both UNIX and Windows based Agent computers by
scanning the file system and comparing file signatures as well as by
querying operating system-specific package registration information.
- Once you have set up Software
Inventory, the software available on a computer can be viewed in the
Information window when Software is selected
- The Detected Applications
window can display:
- Application name
- Units with the application
installed, and location
- Total number of applications
installed (one per Unit and total count) with multiple counts for a Unit
when the application is installed in several different directories on the
hard disk.
Software Metering
- Software licensing
administration is done with the Software Metering feature, which can be
used to:
- Monitor which software
packages and applications installed in your organization are being used
on an Agent
- Measure the usage frequency of
any application, whether it is executed from a server or local disk
- Police the number of copies of
software products that are running on the computers of your enterprise to
comply with license agreements and to save upgrades to new software
because the "real" users are easily identified
- Detect any application
(without specifying) that has been started and stopped on the computer
(Software audit)
- Prevent the use of
unauthorized software (including prohibiting users from installing
software on their own and ensuring that a company uses only the
admissible number of licenses)
- A Software Metering Agent must
be installed and running on each client system. This Agent will log all
necessary activities and communicate through CAM,
RPC, or file share with a central Metering Server, managing the queuing
system. The metering and audit information is logged locally and
transferred to the Sector the next time the system runs the Asset
Management Agent.
- The Metering Agent installs as
a service on Windows 2000/XP/NT computers. However, as a prerequisite, MSI 616b13g
must be installed on this computer.
User Account Inventory
- The User Account Inventory
collects information about users and their state on their computers. It
collects all local users on a computer. If the user is a member of a
domain, domain controller properties like 'full name' or specific
information such as locked user account will be read from the domain
controller and displayed on the Admin Console.
- The information collected by
the inventory is as follows:
- According domain controller if
connected
- All local profiles
- Additional information about
all local/domain accounts, which are found on the local system
- All local groups.
Configuration Files
Backup
- Asset Management lets you
centrally manage system configuration files on your network without
leaving your desk. You can define the names and number of backup copies of
key system configuration files, such as AUTOEXEC.BAT, CONFIG.SYS, WIN.INI,
SYSTEM.INI, or NET.CFG. You can also define specific sets of backup files
by groups, so that you can accommodate the needs of different network
groups and users can be accommodated without having to spend hours
configuring backups on a user-by-user basis.
- Asset Management lets you
schedule a backup or restore action of a specific system configuration,
simplifying the management of multiple system configurations. Asset
Management can back up configuration files in several versions.
Search Facilities
- You can retrieve items from the
database with a standard Find function or with a Query.
- The Unit Type, Domain, Area,
and Name fields are available to define the item to find.
- The File Search option is available
on a Domain console only. The File Search lets you search all files on the
local computer as well as computers connected through the network.
- For advanced searches in the
database, you can set up Queries to find the information that is needed.
Policies
- Asset Management collects a
large amount of valuable data for the Admin Console administrator. It is
often beneficial to have policies to help the administrator focus on
critical data when certain threshold values are exceeded or events occur.
- The Asset Management Policy
System is based on user-defined queries and on predefined events.
- Query-based policies are
defined by designing a query that specifies which criteria must be met to
invoke a policy. As the query checks only the delta data values sent by
agents, continual querying of the database is not necessary.
- Event-based policies consist of
a predefined set of system policies. These predefined system policies are
subdivided into several areas and cannot be deleted or created by the
user. However, they can be modified, using the event policy designer.
- A policy is defined by:
- Linked Query
- Tasks to perform
- Whether policy is invoked
- Header and description of
policy
Asset Management
Reporter
- The Asset Management Reporter
tool extracts inventory information from the Asset Management database.
Using the Query Designer, the user is able to evaluate this data and
specify which fields are provided on the reports. The information
extracted can be filtered, sorted, summarized, and viewed immediately in
the GUI, and can be utilized for report printouts or exporting to other
applications (for example as CSV file or HTML file). Reports are displayed
hierarchically in an Explorer-like tree view, and a number of predefined
result sets can be kept for each report as auto history. In order to
prevent a result set from getting deleted when obsolete, the user can
choose to save it.
- Report generation can be user
initiated or scheduled. Scheduling of reports is done in the Reporter GUI.
The Engine will then initiate the report generation itself, according to
the scheduling properties.
- Using the Asset Management
Reporter, you can create reports based on the following data:
- General - general unit information like Area, Type, Name,
etc. can be included.
- Additional Unit Properties - additional unit property
fields like for example Domain Name or Sector Type can be included.
- Inventory Fields - inventory fields from General, User, or
Template inventory can be added to the report.
- Application - application inventory information like file name,
application version, etc. can be included.
- Job - adds job property fields like for instance job
status or last execution to the report.
- Module - includes module property fields like status
information, last execution, etc. to the report.
- Metering - adds metering statistics information like started,
stopped, usage to the report.
Agent Software
- Asset Management Agent Software
includes, among others, control programs that run on various Asset
Management Agent computers. When it runs, such a control program examines
the configuration of that computer, and executes the sub modules
appropriate to the configuration. The Agent software is normally installed
on a shared network drive, but it can also be installed on each computer
locally.
- The types of Asset Management
Agent Software currently include:
- PC Agents
- Inventory Agents for UNIX and
OpenVMS
- Enhanced UNIX Agents
- Windows CE Agents
- Palm Agents
- Docked Device Proxy Agents
Unicenter Remote Control
Remote Control Admin
Console
- Centralized Policy Management - Remote Control Admin Console
brings remote control administration to a new level by enabling all
clients to be configured from a central management console. The
configuration management is based on policies that are easily applied to individuals
or groups of clients. Administrators can create and manage different
configuration profiles that can be pushed to users and groups requiring
varying remote control capabilities. As new users are added to a system or
group, their remote control capabilities can be automatically
pre-configured and deployed on their desktop.
- Centralized User Management - Remote Control Admin Console
allows administrators to centrally manage remote control users and their
access rights. In one easy-to-use interface, administrators can define
preferences and capabilities different users or user groups have, as well
as define which targets they can control. The centralized, policy-based
approach makes it easy to change the remote control capabilities for a
group of users, such as help desk staff, and ensures that none of them can
take remote control of the IT Department's Windows NT Servers.
- Unicenter Common Services Infrastructure - Remote Control is built on
CA's Unicenter Common Services that provide Enterprise Discovery, Real
World Interface, central alert and event monitoring features, and virus
detection software to further enhance the manageability of remote systems.
All the computers in your Remote Control environment are represented in
WorldView, enabling you to view and manage all your computers from a
single point. You can choose to display them within their Computer Group
or as individual computers. This infrastructure also enables Remote
Control users to seamlessly implement CA's other management applications
including storage, virus protection, software delivery, asset management,
and help desk solutions. Through Event Manager Services, Remote Control
generates a log that provides a central view of all ongoing events.
- User-Friendly Interface - Remote Control Admin Console
provides the familiarity of a typical Explorer-type interface plus many
unique and convenient features, including:
- Tree-Structure Plus HTML
Displays
- Getting Started Taskpad Access
- Product Information Access
- Computer States Icons
Remote Control Managed
Environment
- The Remote Control environment
consists of the Admin Console, management server, the management database,
and an unlimited number of managed agents. Managed agents are computers
running the Remote Control application that communicate with the
management server. The management server retrieves and sends information
about remote control sessions to the management database.
- Communication between the
management server and a managed agent is bidirectional. The management
server sends information that governs remote control sessions from the
database to the managed agents. The managed agents then send event
information back to the management server for storage in the management
database. This functionality provides easy, centralized management for
your entire Remote Control enterprise.
- A managed agent receives
information from the management server about:
- Computer Groups - Each managed agent participates in a Computer
Group. Computer Groups are associated with Access Control Lists that
determine user access to managed computers and Computer Settings that
determine the settings for a remote control session. Unless otherwise
specified, a computer inherits the Access Control List and Computer
Settings from the Computer Group it belongs to.
- Computer Settings - Computer Settings comprise a template of
privileges and options that govern remote control sessions. These
settings can be applied to a Computer Group or an individual computer. By
simply changing the template, all computers associated with it
automatically reflect the new settings.
- Users and User Groups - Remote Control populates
the management database with users and user groups selected from the
Windows NT Primary Domain Controller. These users and user groups are
assigned User Privileges that govern remote control privileges.
- User Privileges - User Privileges comprise a template applied
to users and user groups that determine access privileges for remotely
controlled managed agents.
Computer Groups
- A Computer Group is a
collection of computers that can be managed by Remote Control. With
Computer Groups, you can perform management functions available in Remote
Control Admin Console on multiple remote computers simultaneously. These
functions include applying Computer Settings that govern remote control
sessions, rebooting computers, starting and stopping Remote Control, and
placing computers in listening mode.
- You can easily move computers
from one group to another using drag-and-drop functionality. When you do,
the associate group Computer Settings are automatically inherited,
reducing administrative overhead by setting up the desired configurations
once per group. If needed, you can also apply custom settings to a
computer so that it can be controlled in a different manner than the other
computers in the group.
- Access Control List - For each
Computer Group or individual computer, you can define a list of users or
user groups that can access it. Users and groups are selected from NT
Domain users populated to the Remote Control management database.
Computer Settings
- Computer Settings are Remote
Control preferences and access privileges that are applied to Computer
Groups or individual computers during remote control sessions. Computer
Settings act as a template that allows you to easily administer settings
to a single computer or multiple computers from the Admin Console. By
simply changing the template, all computers associated with it
automatically reflect the new settings.
- You can easily apply a Computer
Setting to a Computer Group or an individual computer by using the
drag-and-drop method or selecting it from the General tab on the
Properties dialog.
- When installed, Remote Control
includes Default Settings. The Default Settings can be used as is or they
can serve as a template from which you can evolve other user-defined
settings. If needed, you can also apply custom settings to a computer so
that it can be controlled in a different manner than the other computers
in the group. Custom settings applied to a computer override the Computer
Settings applied to the Computer Group that the computer is in. If a
computer with custom settings is moved into a new Computer Group, the
computer retains its original settings.
Remote Control Users and User Groups
- Remote Control uses the Windows
NT Primary Domain Controller to provide a list of groups and users.
Through Remote Control's Directory Utility, you can select an NT primary
domain, view its user accounts and groups, and select those that you want
to populate to Remote Control. Remote Control stores information about the
groups and users that you populate in its management database. To keep the
information current, Remote Control provides a Synchronize Utility that
updates the database with any changes that have occurred in NT User
Manager.
- Through the Admin Console, you
can view information about Remote Control users and user groups. They are
represented in the left pane of the main window as the Users resource with
the overlapped profiles icon. When you expand Users, each domain is
displayed with their Groups and Users in a tree structure. Domains and
Groups are also represented by overlapped profiles; Users are represented
by a single profile.
- Once you have populated Groups
and Users to Remote Control, you can associate properties with them that:
- Govern their machine access
rights (using an Access Control List)
- Determine whether they can use
certain Remote Control features (based on their User Privileges)
Remote Control User Privileges
- User Privileges are a set of
standard rules that govern how the Remote Control application behaves on
viewer machines. For example, User Privileges determine:
- The Remote Control functions
that the viewer can perform, including chatting, sending and receiving
files, recording Remote Control sessions
- Whether the Host keyboard and
monitor are disabled during a remote control session
- Whether the Remote Control
application is hidden during a Host session
- User Privileges are used in
conjunction with host preferences, viewer preferences, and computer access
privileges to determine which options and settings the viewer will use
when connecting to a remote host. After the viewer has successfully logged
on and the username and password verified by the NT Domain Controller; the
user, host, computer, and viewer privileges are combined to determine the
access rights of the viewer.
Access Privileges
- Access Rights determine the
remote control settings a viewer uses when connecting to a host computer.
Access Rights are comprised of four sets of privileges configured in the
Admin Console and the viewer computer. Once a user attempting a remote
control session has been authenticated by NT security and verified as a
member of the appropriate Access Control List, Remote Control checks the
Access Privileges.
- The four sets of privileges
that make up Access Privileges are:
- Machine Access Privileges (MAP) - Machine Access Privileges
determine the types of Remote Control functions (such as File Transfer
and Chat) allowed on remotely controlled computers. These privileges can
only be set in the Access Privileges folder in the Admin Console. Visible
is the only attribute that can be assigned to Machine Access Privileges.
- Host Preferences (HSP) - Host Preferences determine
whether the viewer can control computer and peripheral operations on the
host computer. Host Preferences include options such as printer
redirection, behavior of the host mouse, and session recording. They are
set in the Host folder. Host Preferences can be set to Visible, Agent
Writable and Viewer Negotiable. If a privilege or option is set to Viewer
Negotiable, User Group Privileges are applied.
- User Group Privileges (UGP) - User Group Privileges
determine the remote control functions (such as File Transfer and Chat) a
user can perform. They also determine the computer and peripheral
operations a user can control on the host computer. User Group Privileges
can be set to Visible and Viewer Negotiable. If a privilege or option in
User Group Privileges is set to Viewer Negotiable, then the Viewer
Preference is applied. See Determining User Privileges, later in this
chapter, for more information.
- Viewer Preferences (VWP) - Viewer Preferences
determine the computer and peripheral operations the viewer can control.
If a privilege or option is set to Viewer Negotiable in Host Preferences
and User Group Privileges, the settings in the Viewer Preferences apply.
Viewer Preferences are set in the Viewer folder.
Remote Control Statistics
- The Remote Control Admin
Console stores two types of data about your managed environment - the
Session Log and Session Information.
- The Session Log records
connection information forwarded from the Host's Event Log. This provides
a centralized record of connections made within your environment for easy
management. Connection information is stored in the RCSession.LOG file. It
can also be written externally to the NT Event Log or the Unicenter Event
Log.
- Session Information
automatically tracks the status changes of all managed nodes within your
Remote Control environment and displays the computer connections information,
including:
- Host - Host name
- Viewer - Viewer name
- Started - Connection start
time
- Duration - Connection length
- Remote User - Computer name
Advanced Installation
- In addition to the Installation
Wizard, Remote Control also provides you with the following alternative
ways to install the product.
- Silent Install - The silent install feature installs Remote Control
on a target computer without any operator intervention. You can use it in
a stand-alone environment or as part of a software delivery system. Using
the silent install, you can install the manager, the agent, or both
- Remote Install - Enables you to perform an unattended install on a
group of remote computers
Unicenter Software Delivery
Features of Software Delivery
- Software Delivery provides an
automated solution to many of the problems inherent with performing manual
distributions. Using Software Delivery you can:
- Work with existing Windows and
UNIX servers to access and administer programs installed on remote
computers.
- Track all software installed
at a particular location and identify when, where, how, and by whom the
programs were installed.
- Distribute new software
packages and upgrades of existing packages to all or to a selected group
of computers from a central location or through local administrative
computers.
- Maintain a centralized record
of all software installed in the Software Delivery network, regardless of
whether or not it was installed through Software Delivery.
- Monitor logged events that
track the installation and activation of item procedures associated with
programs registered in the Software Library.
- Identify installed software
that has not been distributed or registered through Software Delivery.
- Generate an installable
software image containing all required product files and system
configuration changes, using the Software Management Packager, available
for Windows and UNIX platforms.
- Perform an unattended
installation of Windows computers with PXEenabled network interface,
using Operating System (OS) Installation Management.
- Create and edit software
distribution scripts and register them in the Software Library, using the
Desktop Management Script Generator and Desktop Management Script Editor.
- Implement security in your
Software Delivery system, using Software Delivery Security features.
- Expand Unicenter NSM
capabilities, which include monitoring Software Delivery events and
responding to selected event messages, customizing the view of your
Software Delivery environment, securing resources, and generating
reports.
- Utilize the functionality of
other products such as Unicenter Asset Management, Unicenter Remote
Control, and Data Transport Service (DTS) to further enhance your
Software Delivery capabilities.
- Integrate with Unicenter
ServicePlus Service Desk, to raise trouble tickets on job or distribution
failures. The Software Delivery Administrator is enabled to context
launch into the Unicenter Service Desk Web browser to view trouble
tickets associated with a job target or job container.
Simplified Software Distribution
- Software Delivery provides a
flexible, scalable, and open means of handling software distribution and
control across networked environments. Software programs are defined to
the Software Delivery Software Libraries maintained on dedicated Windows
and UNIX file servers; from there they can be distributed easily, as
needed, to your target computers.
- Software Delivery provides a
flexible, scalable, and open means of handling software distribution and
control across networked environments. Software programs are defined to
the Software Delivery Software Libraries maintained on dedicated Windows
and UNIX file servers; from there they can be distributed easily, as
needed, to your target computers.
Control and Uniformity
- In addition, Software Delivery
provides control and uniformity in your network, allowing the Enterprise
Administrator to keep track of all authorized program installations. You
can schedule software packages to be delivered to, installed, activated,
or configured on any computer in the network, and then check to see if all
these tasks were performed. As part of this procedure, you can also make
sure all users have the same version of a software package.
- Moreover, you can search for
and remove old versions of authorized software, clean up failed installations,
or detect unauthorized versions of software, on any computer in the
Software Delivery system.
- All these capabilities provide
a far greater measure of control and uniformity than any LAN or WAN alone
can offer.
Centralized Distribution
- Programs can be stored directly
in a Local Library for distribution to all computers networked to the
Local Server, or they can be initially stored in the Enterprise Library,
where they can be distributed throughout the network of areas. Items that
are first registered in the Enterprise Library can be distributed to Local
Libraries.
- Programs can also be stored in
a Workgroup Library for distribution to all computers networked to the
Workgroup Server. Jobs set up on a Local Server can also be distributed to
the Agents of a downstream Workgroup Server.
- Software Delivery also lets an
administrator detect what programs are currently installed on a particular
computer, regardless of whether or not they were installed using Software
Delivery.
Inventory Database
- A separate Software Delivery
database is maintained on the Local, Workgroup, and Enterprise Servers and
contains libraries, folders, and log files.
- Software Libraries - Store the software programs that are
available for distribution. The Enterprise Server contains the Enterprise
Library, the Local Server contains the Local Library, the Workgroup
Server contains the Workgroup Library, and the Staging Server contains
the Staging Library.
- Folders - Maintain records of important server data, such as
computer attributes. The information recorded depends on the type of
server.
- Log files - Record the occurrence of events, such as the
successful or unsuccessful installation of a product.
Inventory Discovery
- Inventory Discovery is a tool
that uses customizable detection and verification scripts to search for
the presence, or optionally, the absence of particular software packages
on a target computer. Inventory Discovery is most commonly used to
determine which software programs were installed without intervention of
Software Delivery.
Software Management
- Software Management guarantees
full control of heterogeneous environments and is the best way to maintain
large infrastructures.
- Software Management helps you
to install, configure and remove software throughout a complex environment
in a controlled and standardized way. Software Management is based on the
components Packager and Installer that are both available for Windows and
UNIX. Packager and Installer are Software Management tools that enable you
to create software products, and to easily install and remove them
unattended and reliably.
- With the Packager component
products can be created for Windows and UNIX platforms. During the
packaging process, the product to be packaged is installed on the same
computer as the Packager. Product files, installation parameters, and
other necessary changes can be specified. The Packager then records the
information required for a successful installation of the package, and
generates an installable software image. Note that the software image can
only be installed on target computers that run the same operating system
as the packaging computer.
- Software and data for Windows
are packaged in the SXP format. For UNIX, software and data are packaged
in the PIF (product interchange file) format.
Operating System (OS) Installation Management
- Operating System (OS)
Installation Management enables you to perform an unattended initial
installation of a Windows computer with PXE-enabled network interface, and
an automatic integration in Software Delivery. By using OS Installation
Management, it is easy to deploy and to configure the infrastructure (that
is, Boot Server, boot images, OS images, and configuration parameters) to
be able to manage unattended a great number of Boot Servers and Target
Computers. OS Installation Management consists of the following
components:
- Image Prepare System
- Boot Management Explorer
- Boot Management Server
- Boot Server
- Target Computer
Desktop Management Script Generator and Editor
- The Desktop Management Script
Generator is a tool that enables you to easily record configuration
changes for an installed product, for example, registry modifications. The
Script Generator takes a snapshot of the computer and builds an image and
installation script. This script can then be registered in the Software
Library, and installed on target computers that have the appropriate
script interpreter installed. The Desktop Management Script Generator is
not suitable for complex product installations.
- The Desktop Management Script
Editor can be used to write, syntax-check, debug, and run scripts.
Security
- Software Delivery Security
features can be used to secure your Software Delivery system. Using
Software Delivery Security, you can create security groups to determine
which operating system dependent groups and users will have access to the
Software Delivery system. You can establish class permissions, as well as
folder and object permissions. You can also use SD Security to restrict
views within the SD Explorer.
Unicenter NSM Integration
- Unicenter Software Delivery
integrates with either Unicenter TNG 2.4 or Unicenter NSM, a
comprehensive, open management solution that provides cohesive, integrated
administration of all IT resources in your enterprise. Alternatively, for
a true standalone solution, Software Delivery comes complete with CA
Common Services (CCS). CCS offers all the crucial components of Unicenter
NSM necessary to satisfy the requirements of Software Delivery.
Specifically, CCS components supplied include Event Management, Calendars,
WorldView and AutoDiscovery, Unicenter Explorer and Anti-Virus.
Asset Management and Remote Control Integration
- Software Delivery can be
integrated with Unicenter Asset Management and Unicenter Remote Control.
The integration with Asset Management, for example, allows for computer
group membership to be resolved using Asset Management queries.
Data Transport Service Integration
- Data Transport Service (DTS) is
the data transfer tool that controls the flow of data transfers in the
Software Delivery system. Therefore, the Data Transport Service
Administration Client is completely integrated in the SD Explorer (DTS
Administration). Data Transport Service supports point-to-point data
transfers, as well as point-to-many data transfers including Broadcast,
Multicast, and Fanout. You can also optimize network performance by
throttling parcel sends and restricting parcel size.
- Additionally, through the
integration of Data Transport Service with Software Delivery, you can
halt, resume, and terminate data transfers from the Software Delivery
dialogs.
Unicenter ServicePlus Service Desk Integration
- Software Delivery can integrate
with Unicenter ServicePlus Service Desk from Version 6.0, which provides a
single solution to manage trouble tickets, that is, requests and change
orders, throughout the enterprise. The Unicenter Service Desk integration
allows Software Delivery to raise trouble tickets on job failure or
distribution failure, and to attach logs to trouble tickets. The Software
Delivery Administrator is enabled to context launch into the Unicenter
Service Desk Web browser, so that he can immediately view trouble tickets
associated with a job target or job container. On the other side, the
Service Desk Analyst is enabled to locate failed job targets and job containers
quickly.
Install Model
- Open installation mode:
- The open installation mode
supports any software installation. Software Delivery relies on the
vendor-provided install methods, for example to perform an upgrade, and
thus only installs files that are new or changed from the previous
installation. When using the most widely accepted install routines, such
as Install Shield, only the necessary (new or updated) files are copied
and installed.
- The open installation mode
also supports MSI, Windows CE, Palm, and Nokia software products. During
registration of the product in the software library, you can choose one
of the available installation methods.
- Managed installation mode:
- The managed installation mode
is based on Software Management, and uses the Packager and Installer
components. These tools are available for Windows and UNIX. The Packager
is used to generate Software Management products (packages), and to
register them in the Software Library. Using Software Delivery, these
products are distributed to, and installed unattended on target
computers.
- Software Management enables
you to install, configure and remove software throughout a complex
network environment in a controlled and standardized way. Both the
Packager for Windows and the Packager for UNIX, provide the delta
packaging feature. A delta product contains only the differences between
two software products or any data, so that reduction of data traffic can
be accomplished.
Graphical User Interface (GUI)
- The benefits and features of
Software Delivery are available to you from the Software Delivery Explorer
(SD Explorer), an easy-to-use graphical interface, and a Web GUI.
- To simplify the access and
performance of the day-to-day tasks of a Software Delivery Administrator,
the SD Explorer on Local and Workgroup Servers provides you with the Tasks
folder, and an incorporated tutorial. When you select Tasks, wizards will
guide you, step-by-step, through each of the relevant administrative
tasks. After installation of the Software Delivery Admin Console the tasks
are available out of the box.
Command Line Interface (CLI)
- Software Delivery supports a
command line approach to managing software. Most of the Local Server
administrative tasks performed through the Software Delivery GUI can also
be performed using commands.
Unicenter NSM
Global Catalog
- Every Unicenter NSM
installation has a central catalog known as the Global Catalog. Created at
installation, the Global Catalog contains information about the
availability and location of all Unicenter NSM components. The Global
Catalog should be installed on a high availability server before
installing any other components such as WorldViewT, Event Management, or
Agent Technology Distributed State Machine (DSM). WorldView, Enterprise
- Management, DSM, and other
information sources register with the Global Catalog as providers at
installation. Providers enable applications, data, and business components
to appear as native within the object infrastructure so that all data can
be accessed and integrated, regardless of origin, format, or location. Any
Unicenter Explorer Client pointing to the Global Catalog can see the
entire Unicenter NSM installation. The Unicenter Explorer Client running
on your PC, for example, may be using a Global catalog on a server
somewhere else. Your local browser can access any provider known to the
Global Catalog.
- Using Unicenter NSM,
organizations can create software agents for devices that do not support
standard management protocols such as SNMP. In fact, you can create agents
to monitor a wide range of devices, such as IDNX switches, modem banks,
video multiplexors, long-range radio transceivers, secure telephone transceivers,
frame relay switches, and DoD encryption devices. Unicenter NSM empowers
organizations to monitor and manage their entire networking
infrastructure, not just typical TCP/IP networks, allowing non-IT devices
to be instrumented for management.
- The robust management functions
of Unicenter NSM span across traditionally discrete resources. The
discovery services in Unicenter NSM, for example, discover systems,
databases, and applications, in addition to network devices and topology.
This complete inventory of IT resources allows administrators to manage
from the perspective of "the big picture."
- In addition to TCP/IP,
management functions must support heterogeneous environments including
SNA, DECnet, and IPX networks; Windows NT, UNIX/Linux, and proprietary
servers; NCs, Windows desktops and mainframes; hierarchical, relational
and object databases; diverse network devices; web servers from different
vendors; and applications from many different companies. Unicenter NSM
provides a solution that manages all of these resources in a cohesive,
integrated manner.
- The ability to extend and
customize integrated functions is central to the concept of end-to-end
management in Unicenter NSM. For example, discovery agents are extensible
to discover any custom IT resource (such as in-house built applications)
or even non-IT resources such as POS devices, telephony, and even
transportation systems.
Scaleable Infrastructure
- Providing end-to-end coverage
requires a highly scaleable infrastructure to efficiently manage the
diverse scope of resources, which can range from hundreds to thousands
across every major computing platform.
- The Unicenter NSM architecture
makes it possible to develop and deploy both CA and non-CA management
functions in a manner that best suits the enterprise and requirements of
each individual IT organization.
- To address scalability
requirements, Unicenter NSM provides efficient agent architecture for
monitoring resources and invoking policy. Unicenter NSM can correlate
information across disciplines, devices, and the enterprise as a whole,
not only taking automatic actions but also anticipating problems. Recent
advances in software agents, based on adaptive pattern recognition, extend
conventional technology.
Predictive Agents
- Neural networking agents known
as Neugents enable Unicenter NSM to behave as a self-learning system.
Neugents can recognize complex patterns in vast amounts of data, correlate
seemingly unrelated events, predict business outcomes, and learn and adapt
continuously-even when faced with dynamic business changes. Through
Neugents, Unicenter NSM integrates advanced business intelligence logic
into eBusiness infrastructure.
- Incorporating technologies from
statistics and artificial intelligence, Neugents use pattern recognition
to predict opportunities, detect problems, and offer solutions. The
integration of "learning" agents with a cross enterprise framework is
critical to the efficient management of huge, complex environments.
Neugents are available as an option to Unicenter NSM.
Advanced Visualization
- Unicenter NSM uses
visualization technology to turn massive amounts of data into useful and
relevant information. The WorldView component of Unicenter NSM presents a
2D and 3D view of the infrastructure to facilitate intuitive management of
the enterprise. Anyone familiar with Explorer-style and browser-based GUIs
can move effortlessly through systems and networks, without special
navigational skills or prior knowledge of physical topology.
- Organizations can use the
interface that is most appropriate to their management requirements. For
example, organizations that deploy the optional Neugents technology would
probably prefer the 3D Map. The data visualization, animation and virtual
reality capabilities of the 3D Map complement pattern recognition
technology, and the underlying patterns detected in data, especially time
sequences, are more easily depicted using an extra dimension. On the other
hand, a network operator who is frequently on the road troubleshooting and
opening new facilities may prefer a more conventional 2D view solely of
network topology.
- Delivering an extensible
architecture with predictive and self-learning capabilities is just the
beginning. Unicenter NSM also delivers a wide range of rich management
functions for administering various IT resources. The integration of all
management functions allows you to leverage your existing investments in
technologies, tools, data, and proven business logic.
Network Management
- Network managers struggle daily
with the variety of devices supplied by different vendors, diverse
communications protocols, and complex network topologies. The various
platforms, communications protocols, application software, servers,
mainframes, desktops, and databases that can be connected to a network are
infinite.
- Unicenter NSM blends the
management of network elements with system, database, and application
assets to provide a comprehensive, integrated enterprise management
infrastructure. The system treats network elements as part of a continuum
of interrelated components with a full understanding of the dependencies
between them.
- From a single, central console,
Unicenter NSM can manage networks running every major protocol,
automatically discover network elements using these protocols, and map
their network topology.
- You can visualize the network
as a discrete entity in relation to other enterprise assets or within the
context of business processes. Unicenter NSM makes network management
accessible to multiple audiences within the enterprise.
Internet Management
- By extending its robust
management functionality to web sites and across the Internet, Unicenter
NSM allows enterprises to conduct business with confidence in cyberspace.
- The architecture of Unicenter
NSM allows IT departments to transparently encompass web-based (Internet,
extranet or intranet) resources. An effective web presence requires
professionally managed servers in terms of reliability, availability and
performance, including:
- Securing content from loss or
corruption, whether intentional or not
- Eliminating network, systems,
databases or applications choke points
- Providing automated,
policy-based responses to common events such as usage spikes and virus
attacks
- Planning for and positioning
servers around the Internet to minimize traffic hops and application
response time
User Interfaces
- Unicenter Explorer
- Implemented in Java, Unicenter
Explorer integrates and hosts all user interface components and plug-ins
for complete management. You can run the Unicenter Explorer management
console on various platforms in a heterogeneous environment.
- Unicenter Explorer includes
standard menus, context menus, a left-hand pane for navigation and a
right-hand pane for the display of information on objects selected in the
left-hand pane, configurable caption titles, and a paper-look design. You
can launch Unicenter Explorer through the Unicenter TND program group.
UNIX/Linux users can run the uniexplorer script in $JI_SYSTEM/bin to
access it.
- Unicenter Browser
- The Unicenter Browser is an
Internet- and intranet-based user interface that provides virtually all
of the functionality found in the WorldView Classic user interface. Since
it is a Java applet, it does not require client installation, which makes
it accessible from virtually anywhere. Windows users can access it
locally on the system where the Common Object Repository resides through
Start, Programs, Unicenter TND, Unicenter Browser Interface. UNIX/Linux
users can run the tngui script in $CAIGLBL0000/wv/scripts to access it.
Remote systems can access it by entering a URL address on any
Java-enabled web browser in the form: https:// wvserver/ubi/ubi.html where wvserver is the name or IP
address of the web server on which the server components reside. You can
use many of the procedures for the WorldView Classic GUI, contained in CA
Procedures located in the Online Books program group, with this
interface.
- Unicenter Classic
- Unicenter Classic refers to
the traditional Windows-based user interface delivered with previous
versions of Unicenter TNG. Unicenter Classic includes the WorldView and
Enterprise Management program groups accessed through Start, Programs,
Unicenter TND.
- Unicenter Classic also
includes the cautil command line interface.
- WorldView Classic
- WorldView Classic refers to
the traditional Windows-based user interface. WorldView Classic includes
the WorldView program group accessed through Start, Programs, Unicenter
TND.
- Using WorldView, you can do
the following:
Discover
all the devices in your network using the CA Discovery service and automatically
add them to the Common Object Repository as managed objects.
Define
new classes using the Class Wizard, allowing for characterization and modeling
of practically anything.
See
your entire network graphically represented on 2D and 3D maps, grouped into networks,
subnetworks, and segments based on their logical relationships.
Create
customized Business Process Views of specific processes based on different
business needs, resource features, roles, geographical locations,
organizational structures, and applications.
Trace
all events reported by network devices on the Event Console Log, isolate
faults, and display them on the WorldView maps so action may be taken for
resolution.
- WorldView Classic also
includes the cautil command line interface.
End-to-End Management
- End-to-end management is the
ability to identify resources throughout your IT infrastructure and
organize, monitor, and manage them. Typically, these resources are widely
dispersed throughout the enterprise.
- Unicenter NSM uses object
technology to automatically identify and define many resources in your IT
infrastructure.
- Object Technology
- The number of individual
resources in an IT infrastructure may range from small (hundreds) to
large (millions). Unicenter NSM uses an object-oriented approach to the
management of these resources by automatically defining them as "managed
objects" and storing them in the Unicenter Common Object Repository.
- The Common Object Repository
is used by all management functions to store information about managed
objects, their properties, relationships, and the methods by which they
are managed. Examples of managed objects are hardware devices, software
applications, databases, and processes.
- Common Object Repository
- All of the objects in your
enterprise, including network devices, agents, and software applications,
are defined according to their Unicenter NSM class names, and are stored
in the Unicenter NSM Common Object Repository (see Objects and Classes
following). The Common Object Repository contains managed objects derived
from many different classes, such as router, host, application, database,
agent, and link. It also contains policies, methods, associations, and
objects derived from non-managed object classes.
- Building the Common Object
Repository with information about the resources in your enterprise-also
called "populating the repository"-is accomplished using the CA Discovery
service.
- Objects and Classes
- Unicenter NSM uses two basic
tools to manipulate data: objects
and classes. Understanding
this concept makes creating or modifying a class with Unicenter NSM much
easier.
Unicenter
NSM focuses on easily defined units, which together with their status, are
referred to as objects. Examples of
objects include SQL servers and CD-ROMs. Unicenter NSM lets you manage these
objects.
A
class is a collection of objects with the same characteristics and behavior.
There are many types of classes.
A
special type of class is the virtual class. A virtual class is not used to
create objects, but rather used to help you organize other classes. For
example, the ManagedObject class is a virtual class. In Unicenter NSM, you can
use the Class Wizard to simplify the creation of classes.
Unicenter
NSM provides classes for a variety of the most common entities found in
heterogeneous environments. Each predefined class has all the characteristics
defined and is ready to use.
- Advanced Visualization Capability
- Using any data source, you can
transport your entire infrastructure to a virtual reality plane that
simulates real world environments and is both easy to use and to
understand.
- The innovation of the
Association Browser shows the dynamic container relationship and
enterprise configuration through a wide array of views. This advanced
browser allows you to traverse objects in your enterprise.
- Time Dimension
- Time dimension is achieved
through the Historian technology of Unicenter NSM. Presented in a
multidimensional format, Historian gives you unprecedented insight for
the entire enterprise. This added intelligence increases service and efficiency
thresholds.
Agent Technology
- Unicenter NSM uses multi-level,
manager/agent architecture. Agent Technology is critical to the management
of large environments.
- Agents perform remote
monitoring to report to the manager when error conditions occur or certain
threshold values are reached. Agents may also act when instructed to do so
by the manager, or they may correlate information and act by themselves.
- Unicenter NSM provides agents
to monitor operating systems and databases. Using the Software Development
Kit (SDK), you can also create agents for any device or process, as
desired. Unicenter NSM is an open architecture into which you may add
agents created by other software vendors.
- You can create agents to
instrument file systems, database applications, and other software
applications. These agents significantly increase your ability to monitor
and control such software processes.
- Node View
- You can use Node View to
monitor the status of managed objects discovered by the Auto Discovery
process. Managed resources on a node may include such entities as the
operating system and its subsystems, databases, and software
applications.
- Because Node View displays the
managed objects on a node in tree format, you can see both the overall
status of the node, and the logical relationship and status of individual
agents and objects at the same time.
- DSM View
- DSM View is a companion to
Node View and provides detailed information about each managed object in
the Distributed State Machine's domain. You can use DSM View to create
new properties for a managed object as well as modify the values of
existing properties. Using the DSM View windows, you can:
Display
managed objects based on the class to which they belong.
Query
the Object Store for managed objects.
Edit
the properties of a managed object.
- MIB Browser
- The MIB Browser is a graphical
user interface that can be used to view the values of MIB attributes.
Using the MIB Browser, you can browse MIBs supported by SNMP agents
running on any node connected to your Unicenter NSM workstation over a
TCP/IP network, set the values of MIB attributes, and print MIB data.
- Individual Agent Views
- You use the individual agent
views to drill down to the specific set of resources monitored by each
Unicenter NSM agent. You can also use the controls provided by the views
to add new resources for monitoring and to set the threshold values that
determine the status of each of the monitored objects.
- Each agent view is unique and
provides a set of detail windows that reflect the different sets of
monitored agent resources, such as database tables or file systems.
Performance Management
- Performance Management provides
the following graphical applications used for visualization of performance
and resource consumption data:
- Performance Configuration
- Performance Scope
- Performance Trend
- Performance Chargeback
- The Performance Management
agents collect data from standard system utilities appropriate to the
environment being managed. Using the tools provided, you may view this
performance data in a context-sensitive fashion by pointing and clicking
the managed objects on the Unicenter NSM WorldView Map.
Enterprise Management
- Enterprise Management is a
collection of integrated system management functions available through
Unicenter NSM.
- Using Enterprise Management,
you can manage your system resources and add policy-based automation,
security, reliability, and integrity to your environment.
- This management can be
accomplished in a centralized fashion, distributed throughout the network,
or hybridized by combining different approaches to best match the unique
structure of your organization.
- Further, each Enterprise
Management workstation can be customized to reflect the needs of a
particular administrator. For example, one workstation can manage backup
and archiving of storage, while security workstations can be placed
throughout the network, bringing user administration closer to each
business unit.
- Most successful organizations
operate according to established policies.
As the organization becomes more complex, it becomes necessary to
formalize and document these policies. Unicenter NSM allows these policies
to be enforced by the systems management functions available in Enterprise
Management. Some examples of these types of policies are:
- When and how different types
of data are backed up
- Who has access to sensitive
data
- Who can change sensitive data
- How often certain processes
shall run
- What to do if they fail
Enterprise Management Functions
- Event Management is a status/exception management facility. Using Event
Management, you can define policies that instruct Unicenter NSM to
intercept selected messages requiring additional attention.
- By defining Event Management
policies, you can:
Respond
to the message.
Suppress
the message.
Issue
Unicenter NSM commands.
Start
other programs or scripts.
Send
information to a network management application.
Forward
the message to other managed platforms.
Issue
commands to be executed on other platforms.
Define
or update objects in the Unicenter NSM Common Object Repository.
Administer
the Unicenter NSM environment remotely using email and pager messages.
- The CA Event ConsoleT lets you
monitor system events across the network as they occur. All running
programs and user processes can direct inquiries and informative messages
to this facility.
- You can process messages on
individual servers and redirect them to a central server or other
Unicenter NSM Event Management servers and, by extension, their consoles.
You can collect related messages network-wide for display at a single
location, or send them to multiple locations, as needed. Additionally,
you can use Security Management options to restrict Console Log views to
only authorized personnel.
- Workload Management provides an effective tool for planning,
organizing, and controlling your entire production workload. Workload
Management allows you to automate background processing for execution
during non-peak hours or according to pre-set schedules, dependencies on
other jobs, calendar definitions, or a combination of these.
- Using Workload Management, you
can:
Define
and maintain jobs.
View
a list of related jobs.
Identify
predecessor jobs, files, and manual tasks.
Schedule
jobs with calendars and triggers.
Display
job status.
Cancel
or demand jobs.
- Additionally, Unicenter NSM
Security Management can be integrated to provide authority for each job,
and to prevent unauthorized access to these facilities.
- Tape Management provides comprehensive, yet easy to use tools to
perform tasks associated with maintaining your tape library. These tasks
include the following:
View
lists of files, volumes, and storage vaults/areas so you can update or perform
actions based on the information.
Change
the expiration date of a volume.
Check
a volume out to an out-of-area storage vault, or check a volume in that was
previously out-of-area.
Print
an external label for a volume by selecting either the volume serial number or
the data set name.
Update
the cleaning statistics.
Display
the status and service description of a volume (in service, deleted, expired,
scratch).
View
lists of tape devices based on esoteric group or generic unit group name for
which you want to receive detailed information.
Monitor
tape device status to determine whether the device is online or offline.
Monitor
the movement of tape volumes through the Vault Management system.
Place
ANSI standard labels on tape volumes.
Protect
against tape data destruction by malicious or accidental overwrites.
Maintain
automatic tape file inventories.
Facilitate
swift retrieval of the appropriate tape volume when a file is needed.
Provide
for automatic recognition of mounted tape volumes and assignment of those
devices to requesting applications.
- Many installations require some
type of facility for the storage of tape volumes containing critical
files. Examples of such storage facilities include a fireproof vault or an
off-site storage location. Working with Tape Management, Vault Management supports:
Vault
creation
Media
selection
Automated
media movement
Manual
media movement
Movement
and inventory tracking
Audit
trails
- Storage Management comprises Brightstor ARCserve 2000 Backup
Unicenter Edition. Brightstor ARCserve Backup is the backup and restore
management solution for a local Windows or UNIX/Linux host server.
Brightstor ARCserve Backup furnishes the following features:
The
Job Status manager informs you of job activity and assists in controlling a
specific Brightstor ARCserve Backup job.
Various
options let you optimize basic functions, such as backing up specific files or
scheduling a job's performance.
The
Device Manager manages the devices and media needed to run Brightstor ARCserve
Backup efficiently.
Brightstor
ARCserve Backup enables you to optimize the use of your media, and designate a
scheduled backup scheme to coordinate with specific requirements in your
environment.
The
server component monitors the Job, Tape, and Database engines of Brightstor
ARCserve Backup, displaying the status of each.
The
Alert manager reports on the status, results, and activities of Brightstor
ARCserve Backup.
Brightstor
ARCserve Backup recognizes ASM tapes and prevents the tapes from being
overwritten.
- Security Management protects valuable system resources. Using
Security Management, you can identify authorized users and the conditions
under which they may enter the system and access designated assets. By
defining policies for Security Management, you can:
Prevent
unauthorized individuals from gaining access (logging on) to your system.
Ensure
that only authorized personnel can access system data, resources, and other
assets.
Protect
against access abuse by users with administrative privileges.
Provide
a way to audit the use of data and resources. Securable assets may include
physical resources, such as programs and files, and abstract resources, such as
administrative privileges, and other user-definable assets, as well.
- An optional feature, User
Profile Synchronization (UPS), permits Windows, UNIX/Linux, OS/390, and
z/OS nodes to participate in the sharing of password and status updates
to user accounts.
- Problem Management
- Automates the definition,
tracking, and resolution of problems. It provides a framework for accurate
management of day-to-day problems and questions.
- You can continuously improve
the reliability of your computing environment by accurately identifying
the cause of a problem and relating it to a specific hardware, software,
or procedural source. Additionally, you can significantly reduce the time
needed to correct problems by assigning ownership and tracking the
progress of the resolution, and by automatically escalating a problem
until it is resolved.
- Further, as it is integrated
with the other Unicenter NSM functions, Problem Management can identify
problems and potential problems automatically.
- Report Management
- Report Management extends
traditional report/print processes by enabling you to define rules under
which selected pages of a report can be repackaged into "bundles" and
redistributed to designated users using print or electronic mail
facilities.
- Report Management also tracks
report delivery so that the system administrator can monitor the service
provided to users.
- Spool Management furnishes a simplified interface to the
UNIX/Linux spooler lp (or AIX enq) to enable users to access and manage
spooled files, and to provide the systems administrator with a graphical
interface to spool functions.
- Print devices are usually
defined once and updated only when a new printer is added to the system.
When you need to add a new printer, you probably spend an excessive
amount of time just looking up the commands and syntax you need to make
the update. Spool Management simplifies this process and expedites the
overall task.
- Using Spool Management, you
can:
Define,
add, and update print devices.
Manipulate
the printer queues.
ManagedPC
- The ManagedPC feature of
Unicenter NSM lets you effectively administer your PC workstations.
ManagedPC provides the following solutions:
- Automatically detects
ManagedPC operating system installation requests, and provides facilities
to customize those requests.
- Furnishes remote installation
services for a Windows operating system.
- During the Discovery process,
automatically inventories all ManagedPCs in the Common Object Repository.
- Secures images transferred to
client computers using Intel's Boot Integrity Services (BIS) for those
clients that support it.
- Through the Unicenter
WorldView GUI, offers you methods needed to monitor the status of your
ManagedPCs.
- Includes facilities in the
Unicenter WorldView interface that can "awaken" a ManagedPC from a soft
off or sleep mode.
- Furnishes reports that are
specifically customized for your ManagedPC administrative personnel.
The Software Development Kit
- The CA Software Development Kit
(CA SDK) lets you take advantage of the capabilities of Unicenter NSM in
your own applications. The Application Programming Interfaces (APIs)
provided allow access to the WorldView, Agent Technology, and Enterprise
Management components of Unicenter NSM.
- The CA SDK includes three API
sets representing the major components of Unicenter NSM.
- WorldView API - Includes functions and exits that enable
user-written programs to interact with Unicenter NSM, the WorldView maps,
and the Common Object Repository.
- Agent Technology API - Lets you create multi-platform, scaleable
manager/agent applications. The Agent Technology API library provides an
environment in which you may develop agents that communicate with management
applications using SNMP.
- Enterprise Management API - Furnishes access to all of
the management functions and common services supplied in Unicenter NSM,
and facilitates cross-application integration. The Enterprise Management
API library includes functions and exits that enable user-written
programs to interact directly with Enterprise Management.
Unicenter Service Level Management
Distinctive Features
- Java-enabled Web-based User
Interface. You
can access all administrative tasks and operational status monitoring through
the web interface. You can get service level reports from any browser
with access to the management console. Unicenter SLM can present collected
data on resources in easy-to-understand report formats, including tables
and graphs.
- Generic ASCII Data Import
Wizard. You
can consolidate service management for disparate applications and services
through an intuitive graphical interface, enabling Unicenter SLM to be
the focus of your service level initiative. Importing external log data to
SLA reports previously required
advanced programming skills.
- XML Data Import Interface. You can import configuration
information and collected data into Unicenter SLM by formatting
this information in XML. This information needs to comply with a
specific XML schema. A SOAP-based interface lets you load this
information easily from remote systems. This new interface and mechanism
lets you more easily automate the configuration and maintenance of
Unicenter SLM.
- Report Wizard. You can define report groups
and report definitions through an intuitive Report Wizard, which
also simplifies report production.
- Metrics. You can create your own SNMP or
service metric to provide support for user-specific SLA reporting. Unicenter SLM supports Windows 2000,
SAP/R3, MS Exchange agents, and Unicenter agents such as Unicenter Web
Management.
- Metric Charter. You can manage your metrics
using the metric charter, which is an advanced visualization and
analyzing tool for service management metrics. This Java application
provides 2D and 3D animation and charts to highlight service trends.
Visual correlation between service components, such as between services
offered inside and outside a firewall, provides insights into service bottlenecks
as well as useful information to aid capacity planning.
- Report Configuration Tools. You can tailor reports to view
data collected within intervals of interest only, such as business
hours, days or weeks, and you can filter the reports to show the
level of details to suit job function or interest. Unicenter SLM can
present reports on a business' process, geography, organization,
customers, service goals and business hours. Unicenter SLM depicts
each group with descriptive, user-friendly names.
- Extensible Data Collection. You can measure, collect, and
import performance and SLA data from a
wide range of sources, including performance cubes produced by the Unicenter®
Performance Management option. SNMP and service metrics from
applications and services extend service management to an entire eBusiness
infrastructure. You can also import third-party network service performance
data from other applications for end-to-end service management.
- SNMP Metric Wizard. You can create SNMP-based
metrics in Unicenter SLM more easily. The wizard also provides you
with the ability to create an expression. Expressions (in this
context) are MIB variables that together form an arithmetic
expression. This can be single OIDs or combinations. The script language
is a small subset of the Tool Command Language (TCL). The wizard
also provides a MIB browser that can perform online browsing against
SNMP agents.
- Exportable Service Level
Reports. You
can generate service reports in batch mode and upload the reports automatically
to a remote web server.
- Service Incidents Highlights. You can monitor what factors
affect noncompliance. Unicenter SLM highlights periods when
external factors, such as power outages, are responsible for
noncompliance with SLA.
- Calendar. You can use the web-based GUI
to create events. These events can be used by Unicenter SLM to
schedule service incidents, but they may also contain other information.
The calendar is designed to provide functionality needed to store
and lookup calendar (date/time) related information.
- Scalable. You can scale Unicenter SLM.
Distributed data collection and measurement architecture makes
Unicenter SLM a scalable solution for networks, regardless of size.
- Integration. Unicenter SLM integrates with
various Unicenter® Network and Systems Management (Unicenter NSM)
agents and solutions for a unified service view of the entire
ebusiness infrastructure. The ability of Unicenter SLM to integrate
includes the following functions:
- Collects service management
data, automatically, from objects in predefined business process views,
creating new report groups
- Monitors the severity status
of these objects for availability in the context of set SLAs
- Sends potential breaches of SLAs
to the Unicenter NSM Event Management console or to the notifications
workspace in Unicenter® Management Portal (Unicenter MP)
Architecture
- Unicenter SLM has a distributed
architecture that includes the following components:
- Console
- Collectors
- Report Repository
- Database
- The following illustration
shows a console and two collectors. The report repository and database run
on the console system:
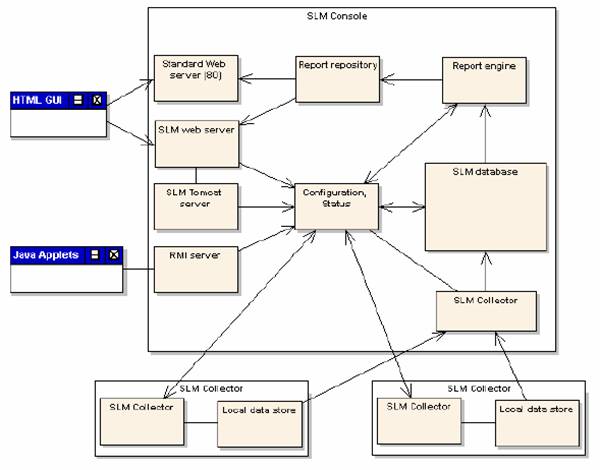
Console
- The console configures data
collections and report groups, produces reports, and monitors current
status. The console contains the configuration database and provides the
following functionality:
- Produces service level reports
- Configures and maintains data
collections
- Displays collected system
status
- Defines and modifies data
collections, report groups, report properties, batch report productions,
and service incidents
- Restarts and stops collectors
- Displays the status of data
collections and Unicenter SLM systems
- Runs and displays reports
- Maintains the report
repository
- Maintains the calendar service
- You access the Unicenter SLM
user interface from any web browser with a network connection to the
console. You access this interface through TCP port 6668.
- You can control access to the
user interface by configuring access control on the Unicenter SLM web
server. By default, access requires a user name and password. The default
for this user name and password are slmo and slmo, respectively.
- Unicenter SLM includes an
interface where you can create user groups using Apache to control access
to specific reports. By creating access groups, you can choose whether a
user has read-only access or writable access to reports.
- The daemon processes on a
console system include the following:
Database
engine (AdvantageTM Ingres® or Microsoft SQL)
Data
collector (smmCollect)
Data
loader (smmdbd)
Report
server (smmReportd)
Web
server (mhttpd)
Optionally,
a standard web server (httpd)
Servlet
runner (Tomcat)
RMI
Server
SNMP
MIB Browser
Collectors
- The Unicenter SLM collector
collects and measures data from a wide variety of sources. Unicenter SLM
regularly uploads this data to the console system for reporting.
- snmpCollect
- The snmpCollect collector
gathers data using an SNMP MIB variable or combination of variables. This
collector can use advanced expressions prior to data logging.
- The pathagent collector measures
IP network delay and availability. This collector sends SNMP traps for
state changes to the management console.
- The appagent collector
measures system and service response time and availability. This
collector sends SNMP traps for state changes to the management console
and can measure a wide range of services such as FTP, HTTP, DNS, SMTP,
NTTP, POP3, TCP echo, NFS, and so forth.
- The coreimport collector
imports objects from a Unicenter® Network and Systems Management
(Unicenter NSM) Common Object Repository (COR) and collects properties
from these objects. This collector must run on the Unicenter SLM console.
- The import collector imports
configuration data, log files, or externally collected data from files.
Reports, Functions, and Services
- Unicenter SLM produces service
level reports and provides the functions and services needed to support
their production. The services provide the following benefits:
- The data model provides a
flexible solution for maintaining, operating, and integrating collected
data and configurations.
- Data collectors gather and
measure statistics from your IT infrastructure.
- Data import reads and uses
data collected by other systems, log files, or additional sources of
information.
- Automated data administration
maintains collected data over time.
- Status view of all data
collections and systems involved provides information vital for
maintenance.
- The web-based user interface
uses, configures, and maintains all aspects of the system.
- Functions group data collections
into report groups and assign them individual service goals and business
hours.
- An automated report production
environment distributes service level reports as web documents.
- Functions support your service
level reporting process, including the ability to comment on and classify
service incidents, export reports to other web servers and enforce
quality control before reports are distributed or exported.
Report Repository
- The report repository stores
and organizes all produced reports. Installed with the Unicenter SLM
console, the report repository contains reports as HTML documents
organized into categories by group, period, and type. You access reports
through the Unicenter SLM web server (port 6668) or a standard web server
(port 80).
- You can create user groups
using Apache to control access to the report repository. When a user logs
into Unicenter SLM, only those access groups that the user is a member of
appear under the Report Repository node of the Unicenter SLM tree.
Database
- The database stores and
maintains all configuration information and collected data. During
installation, you select whether Unicenter SLM bases the database on
either the Advantage Ingres database or Microsoft SQL server product.
- You can install your database
remotely as a regular or clustered database. You must manually configure a
remote database.
Unicenter ServicePlus Service Desk
Unicenter ServicePlus Service Desk Server
- Your Unicenter ServicePlus
Service Desk installation has one or more server components. The number of
servers depends on your enterprise. Every installation has exactly one
primary Unicenter ServicePlus Service Desk server that manages the overall
functionality of the service desk, and installations can optionally have
one or more secondary servers to manage specific features.
- For example, your particular
configuration may be as simple as a single machine on which all the needed
services are installed. This would be the primary server. On the other
hand, your installation may be spread out over several machines, each of
which serves a specific function. For example, you may have one machine
that runs as the primary service desk server, which also acts as your
database server, while a separate web server machine runs the web
interface, and yet another machine authenticates users as they come into
your service desk system.
The Business Structure
- ServicePlus Service Dsk has the
following components:
- Sites
- Locations
- Organizations
- These objects have a
relationship to each other, as shown in the following diagram:
- A site is a grouping of
locations. Because locations reference sites, you should define sites
before locations. This lets you use the new site in the location.
- Locations precisely identify a
specific physical place, such as the address of a particular company, or
an office address.
- Locations are used to pinpoint
where other system components reside, such as contacts and assets. A
location can be any type of place, such as a city, a campus, a building,
or even a floor of a building. Defining locations lets you keep track and
administer the areas and locations where the items of concern to your
enterprise reside. Locations are the only objects with which you can
associate a physical address-all other objects, such as organizations,
assets, and contacts, derive their address from the associated location.
- Locations are also used for
the purpose of automatically assigning requests. To base automatic
assignment on location, you assign locations to request areas and groups.
The request area locations are used to match a request to a location
based on the location of the request's asset or affected end user. The
group locations are then used to select a group that is eligible for
automatic assignment of requests in that location.
- Organizations describe
internal departments and divisions or external companies that can be
assigned to tickets, asset classes, and contacts (for example, they are
used to identify the company with which a customer is associated).
- You can assign a default
service type to an organization that is automatically assigned to tickets
when the organization is specified. This lets you associate a specific
level of service to a ticket based on the assigned organization.
The Business Infrastructure
- An important aspect of
implementing your service desk using Unicenter ServicePlus Service Desk,
is to define your business infrastructure by setting up:
- Asset families and classes
- Manufacturers and models
- Service statuses
- Vendors and vendor types
- Assets
- These objects have a
relationship to each other, as shown in the following diagram:
- Asset Families and Classes
- Asset families classify your
system assets by type and assign meaningful attributes for each asset.
Asset classes identify general categories of assets that your enterprise
supports. Families are broad categories of assets, such as hardware,
software, and services. Classes are more specific categories within the
broader family category. For example, the asset family hardware might
contain asset classes such as, modem, router, repeater, and bridge.
- Organizing your assets into
families and classes makes it easier to manage your assets. For example,
you can generate a list of assets that belong to a particular family or
class.
- Manufacturers identify the
manufacturers of the various assets of concern to your enterprise. Models
contain specific information about the products that a particular
manufacturer provides to your enterprise. For example, you might define
as a manufacturer a particular software company. Then, you would define
as models each one of the applications that the company provides for your
enterprise.
- Defining manufacturers and
models makes it easier to manage your assets. For example, you can
generate a list of models provided by a particular manufacturer and
generate a list of assets of a particular model.
- Service statuses identify the
readiness condition of assets, such as in service, in repair, or
discontinued. Defining service statuses let you track the availability
and use of assets in your enterprise. For example, you can generate a
list of assets that are currently in repair.
- Vendor types are
classifications for vendors that identify the type of company providing
assets. For example, you might classify vendors that you lease assets
from as lessors, while classifying vendors that provide service to you as
providers.
- Vendors identify the companies
that supply your enterprise, including the type of company and a primary
contact. Besides being referenced by assets, you can also reference a
vendor in a user's contact record.
- Defining vendor types and
vendors gives you a convenient way to organize your assets. For example,
you can generate a list of vendors that fall under a particular vendor
type and generate a list of assets from a particular vendor.
- Assets are the devices,
software, and services that make up your business infrastructure. The
information associated with an asset uniquely identifies the asset and
indicates its precise location. Assets are referenced in tickets and can
be associated with contacts (private assets) and organizations (shared
assets). Assets let you:
Identify
assets by name, class, and family
Specify
inventory information
Specify
additional properties to define the asset
Log
and view comments associated with the asset
Specify
location information for the asset
Specify
service information, such as a service type, for the asset
View
and define contacts and organizations assigned to the asset
Identify
hierarchical relationships between assets
View
tickets associated with the asset
- You can integrate your
Unicenter ServicePlus Service Desk installation with other asset
management tools such as Unicenter Network and Systems Management, Unicenter
Asset Management, and Intraware's Argis IT Asset Management Suite.
Policies
- A key component of running your
service desk using Unicenter ServicePlus Service Desk is implementing your
policies in a way that best matches your current business process. You
define policies using the following features:
- Notifications
- Service level agreements
- Security
- Surveys
- Unicenter ServicePlus SD
provides an out-of-the-box policy implementation that is acceptable for
some sites and serves as a good starting point for other sites. You will
need to review the default implementation in all the policy definition
areas to determine if it meets your needs and modify it accordingly, if it
does not.
- Notifications
- With Unicenter ServicePlus SD,
you can automatically notify key personnel about ticket activities
(researching, escalating, and so forth) and events (opening a ticket, for
example). When a significant activity or event occurs, Unicenter
ServicePlus SD creates a notification message that does the following:
Identifies
the ticket activity or the notification event
References
the ticket
Optionally
includes other information
Can
identify potential contacts
- Notifications Methods
- The standard notification
methods for Unicenter ServicePlus SD are as follows:
Email
sends messages by electronic mail directly to the recipient through Simple Mail
Transport Protocol (SMTP) mail. Messages are also sent to the recipient's
notification log.
Fax
sends messages to the recipient using the FAXserve product.
The
notification function sends messages to the recipient's notification log that
the recipient can access when Unicenter ServicePlus SD is running.
Pager
email sends email to an address maintained by a paging system provider. The
email text will typically display on an alphanumeric pager.
- You can also create your own
notification methods. For example, you can send notification to a
particular printer for periodic collection or by pager.
- Service Level Agreements
- In Unicenter ServicePlus SD,
you set up service level agreements (SLAs) using service types and
events. You can
Monitor
tickets using events
Keep
track of vendor and organization commitments and schedules as they relate to
specific tickets using service types
Establish
date and time controls for processing events and service types
- Security
- Before you allow people to
begin using Unicenter ServicePlus SD, it is important that you set up
security to determine what aspects of the system you want users to be
able to access, what level of access you want them to have, and how you
want them to be authenticated when they log into the system.
- Security that you establish
for Unicenter ServicePlus SD applies to all interfaces to the product,
including the administrative client, the web interface, and the email
interface.
- Access Types. Using access types, you can control all
security-related aspects of your service desk, including:
Access
and grant levels
Web
interface defaults
Function
access privileges
User
authentication
Internal
logs
Customization
form group
Unicenter
ServicePlus integration
Data
partition
- Access and Grant Levels. Each access type has an access
level associated with it, as well as a grant level, which you choose from
the following list of predefined access levels, ranked from the highest
to lowest level:
Admin
(highest)
Analyst
Cust/Emp
None
(lowest)
- Function Access Privileges. The access type also defines
function access, which determines the Unicenter ServicePlus SD
components a user can view or modify.
- User Authentication. Unicenter ServicePlus SD
provides a user authentication solution that you can customize as part of
the access type. The same authentication is used by all Unicenter ServicePlus SD
interfaces, as well as by other Unicenter ServicePlus products, such as
Collaboration Tools (Unicenter
ServicePlus CT) and Knowledge Tools
(Unicenter ServicePlus KT).
- Surveys
- Customer surveys are a useful
administrative feature of Unicenter ServicePlus SD, allowing you to
systematically collect and analyze customer feedback about your service
desk performance. As with most other features of Unicenter ServicePlus
SD, you can tailor this one to suit the needs or your site.
Users
- An important part of
establishing a working service desk is defining the users who are going to
access it. In Unicenter ServicePlus Service Desk, users are called
contacts.
- Contact Types. Contact types are used to categorize service desk
users into logical groupings based on how they use the system. For
example, some of the many contact types that are predefined by the system
are analyst, customer, and group. These predefined contact types will meet
the needs of most service desk implementations; however, if your
circumstances require it, you can create new contact types, as well as
modify the predefined contact types.
- A user's contact record defines
all the information the system needs to know about the user, which in
turn, is used in many ways throughout the system
Basic
Identification Information
Login
Information
Security
Information
Service
Type Information
Automatic
Assignment Information
Information
on How to Send Users Notification Messages
Information
about the Assets Users Have in Their Environment
Groups
to which a User Belongs
- A group is a collection of
contacts that represent a specific area of responsibility within your service
desk. Defining groups lets you assign responsibility for resolving a
ticket when that responsibility is shared among several individuals. The
individual that responds to the ticket in the group is irrelevant.
- In Unicenter ServicePlus
Service Desk, groups are implemented using the predefined group contact
type, making a group just a special type of contact. A group has the same
basic information as a contact, with the important additional feature
that groups are one of the keys to automatically assigning requests.
Support Structure
- The support structure of you
service desk consists of the components that your users work with to
resolve problems.
- The support structure of you
service desk consists of the components that your users work with to
resolve problems.
- Unicenter ServicePlus SD
supports the following service desk models:
- An internal service desk
supports employees who work for a company and have questions or problems
with the products and services provided to them by the company. In
Unicenter ServicePlus SD, the request is the basic unit of support when
operating an internal service desk. Requests are tracking documents
designed to handle the questions or problems of employees. They are
oriented toward supporting an infrastructure owned and administered by
the support organization.
- An external service desk
supports customers who buy products or services from your company and
have questions or problems with those products or services. In Unicenter
ServicePlus SD, the issue is the basic unit of support when operating an
external service desk. Issues are tracking documents designed to handle
the questions or problems of customers. They are oriented toward
supporting products and services purchased by the customer.
- Some companies have the need
to operate both service desk models. In these cases, you can choose to
separate these two functions with separate service desk installations, or
you can set up Unicenter ServicePlus SD to support both models. The
latter choice is convenient if your service desk analysts are
cross-trained to support both employees and customers and if the
distinction between internal and external support is not always clear.
For example, you may have employees who purchase products from your
company or customers who have problems and questions with the
infrastructure of your company.
Reports
- Unicenter ServicePlus SD
provides a variety of reporting capabilities. Several reporting options
are built directly into the Unicenter ServicePlus SD administrative client
and web interfaces, including the ability to print forms for individual
change orders, issues, requests, assets, and so on; to display summary or
detail reports for lists of change orders, issues, requests, assets, and
so on; and to display analysis reports.
- In addition, you can install
predefined Microsoft Access and Crystal Reports. These reports present you
with information about the performance and status of your service desk and
are available to you without the need to install any additional
software-everything that you need to run them is installed for you
automatically when you choose to install these reporting options with
Unicenter ServicePlus SD.
- Finally, because all of the
information that you enter and use to run your service desk is stored in
the Unicenter ServicePlus SD database, you can report on that data using
any third-party reporting tool that is compatible with your database. To
facilitate this type of reporting, several convenient views of the
database are provided. Creating reports based on these views is quick and
easy because the complex joins and selections are done for you, presenting
the information that you, the Unicenter ServicePlus SD
clients, have asked for most often.
- Database Views
- To allow you to create
customized reports of the database quickly and easily, several database
views are provided with Unicenter ServicePlus SD. Views simplify access
to data by flattening normalized relational data to hide complex data
relationships without increasing the size of the stored data.
- Unicenter ServicePlus SD gives
you the ability to customize various data formats on the reports you
print from the administrative client and web interfaces
- Summary and Detail Reports
- Summary and detail reporting
options are built into the Unicenter ServicePlus SD
administrative client and web interfaces. To print or view summary and
detail reports, you must first select the records you want the report to
include.
- Analysis reporting options are
also built into the Unicenter ServicePlus
SD administrative client.
Analysis reports help you to provide a global and detailed perspective on
the service desk process. The following analysis reports are available:
Request Reports. Request reports provide you with
statistics, such as number of requests opened, number of requests closed,
average time open, and average time until closed for a specified period. This
report is sorted by date, oldest to newest.
Request Area Reports. Request Area reports provide you
with the number of requests opened in the specified period for each request
area. This report is sorted alphabetically by request area.
Request Area Priority Reports. Request Area Priority reports
provide you with the number of requests opened by priority in the specified
period for each request area. This report is sorted by priority (highest to
lowest) and then alphabetically by request area.
- Microsoft Access and Crystal Reports
- Unicenter ServicePlus SD
includes several predefined Microsoft Access and Crystal Reports that you
can use to generate a variety of graphical and text-based reports. When
you install Unicenter ServicePlus SD, you can choose to install either or
both of these types of reports-this reporting option is available on both
client and server installations.
Options Manager
- The Options Manager is a
feature of the administrative client that lets you modify the
functionality of Unicenter ServicePlus SD. For example, you can specify
that service types are to be applied to requests but not to change orders.
- All options can be installed,
modified, or uninstalled. Some of them require a value to be specified
when they are installed or modified. The detailed description of the
option, available through the online help, indicates whether the option
requires a value, and the values that are accepted by the Options Manager.
- Using the Options Manager, you
can:
- Review the status of all
options at the summary level
- View the details of any
specific option
- Uninstall any of the available
options
- Install any defined option
Integrating Unicenter ServicePlus Products
- Unicenter ServicePlus Service
Desk is one of several Unicenter ServicePlus products and as such, is
closely related to and integrated with other Unicenter ServicePlus products,
such as Unicenter ServicePlus KT and Unicenter ServicePlus CT. Unicenter
ServicePlus KT provides you with the tools you need to manage and search
your knowledge base, and Unicenter ServicePlus CT gives you a personalized
way to interact with customers and help them solve their problems. Used
alone, each of the Unicenter ServicePlus products provides a powerful
solution to help you service your customers-used together, they provide
customers and analysts with all the tools they need to solve problems
quickly and communicate effectively with one another.
- There are a number of different
combinations of the Unicenter ServicePlus products from which you can
choose, depending on your requirements.

- Software Delivery and Service Desk Integration
- Unicenter Software Delivery
provides a single solution for the distribution of software packages
throughout the enterprise. The Unicenter Software Delivery integration
with Service Desk lets Software Delivery raise trouble tickets,
specifically in regards to requests and change orders on a Software
Delivery job failure or distribution failure. Further, the Software
Delivery Administrator is enabled to context launch into the Unicenter
Service Desk Web Browser so that you can immediately view trouble tickets
associated with a job target or job container. On the Service Desk side
of the integration, the Service Desk Analyst is enabled to locate failed
job targets and job containers quickly from the context of these tickets.
- Service Desk and Asset Management Integration
- Unicenter Asset Management
provides a single solution for the discovery and management of IT assets
throughout the enterprise. The Unicenter Asset Management integration
with Service Desk lets Asset Management raise trouble tickets,
specifically; requests and change orders in two ways:
Interactively. From an Asset Management asset,
Asset Management analysts may launch the Unicenter Service Desk Web Browser to
create new tickets associated with the Asset Management asset.
Non-interactively. Unicenter Asset Management analysts
may define Asset Management policies (event or query based) that when violated,
generate tickets from ticket templates in Service Desk.
Graphical User Interface
- You can access all Unicenter
ServicePlus SD functions through its graphical user interface (GUI), which
provides a comprehensive and consistent interface for the Unicenter
ServicePlus SD administrator and service desk analysts.
- The Unicenter ServicePlus SD
GUI and browser interfaces let you customize windows and view information
according to the demands of your business. This lets your administrators
and managers evaluate enterprise-wide problem management status instantly
and respond with resource allocation adjustments when necessary. You can
use the Screen Painter to change windows or create new windows according
to the needs at your site.
Web Interface
- The Unicenter ServicePlus
Service Desk web interface (also called the browser interface) provides
you with Unicenter ServicePlus Service Desk functionality through the World
Wide Web, including the ability to open, update, or close tickets, display
and post announcements, and access supporting data tables. It enables
independent browsing of the knowledge base, thereby reducing the number of
calls to the service desk and speeding resolution times. Web interface
security is controlled by the use of access types. The interface can be
fully tailored and can be used with many popular web browsers.
- The Different Web Interfaces
- Unicenter ServicePlus Service
Desk provides several separate web interfaces for different types of
users. These interfaces differ primarily in their level of access to the
capabilities of the product and the types of tickets they use-interfaces
geared primarily toward a user in an external service desk environment
would work with issues, while internal service desk users would work with
requests and change orders.
- The supplied interface types
are as follows:
Analyst
Web Interface
Customer
Web Interface
Employee
Web Interface
Guest
Web Interface
Mobile
Device Web Interface
Keyword Search
- Unicenter ServicePlus Service
Desk - Keyword Search is part of the Unicenter ServicePlus suite of
products from Computer Associates that offers a complete customer
relationship management solution. Unicenter ServicePlus Service Desk -
Keyword Search (Unicenter ServicePlus Service Desk KS)
is a powerful knowledge management solution that offers multiple knowledge
models, tailoring the right solution to the customer effectively and
efficiently. It enables rapid searches of a dynamic knowledge base to
quickly resolve customer issues.
- Unicenter ServicePlus Service
Desk - Keyword Search is composed of the following modules:
- Search Tool. The Keyword Search method allows you to perform a
search on words contained in the Problem field of knowledge base
documents.
- Managing Documents Functionality. An analyst and knowledge
engineer can manage the content for all of the problem-solving models in
the knowledge base. The Manage Documents function provides a mechanism
for building and editing knowledge underlying the retrieval tools.
Because it includes the ability to assign ownership of a particular
knowledge solution to an expert, it ensures that the solution for a given
problem is kept current and accurate.
- Keyword Search Administration. Keyword Search Administration
enables the knowledge manager and system administrator to manage the
Keyword Search Tools system. A knowledge manager can manage the noise
words, special terms, and synonyms that will be excluded or included in
searches. The system administrator has access to all of the Keyword
Search Administration features, which allows for the management of
documents, attachments, and search terms.
Auto Assignment
- The Auto Assignment feature
helps the Unicenter ServicePlus Service Desk manager become more
productive by reducing the time it takes to administer the assignment of
Requests. Fewer hours are required for manually balancing staff workloads
and coordinating Analyst work schedules.
- Auto Assignment can make
logical choices when it comes to assigning Requests to Analysts, based on
the following considerations:
- Which group of analysts works
on the requests
- When different types of
problems are worked on
- Which locations service the
various customers
- Individual analyst workload
and availability
- Auto Assignment can be
implemented gradually. In other words, you can avoid spending months on
planning and then crossing your fingers when it comes time to start it.
Using the Request Area, Auto Assignment is able to make decisions based on
logical relationships between Analysts, Groups, Locations, and Workshifts.
Whether you track Requests by customers or have an Asset-centric service
desk, Auto Assignment can simplify even the busiest help center.
Unicenter Service Management
(Unicenter
Service Catalog , Unicenter Service Accounting , Unicenter Service Assure ,
Unicenter Service Meter & Unicenter Service Fulfillment )
Unicenter
Service Management is a fully automated and integrated, multi-vendor service
management solution that lets you closely link IT operations with business
requirements. With Unicenter Service Management software, you can track
resource usage by user, Business Unit or line of business, set and manage
service levels and gain visibility into the costs of the services that you provide.
- Unicenter Service Management enables enterprises with:
- Service Provisioning. The automatic activation of
service requests to speed deployment and minimize the amount of time the
IT staff spends on administrative procedures.
- Accurate Accounting of IT Resource Utilization. Enables enterprises to
consolidate and reallocate IT resources, based on actual IT resource
usage. Enterprises gain the ability to manage all of their dedicated and
shared infrastructure resources including network, storage, servers, and
applications. Unicenter Service Management provides enterprises with an
accurate account of how resources are being utilized (i.e. by what
applications, user, or business function)
- Cost Allocation and Chargeback. Enables enterprises to
account for IT expenses and the true cost of providing services and
distribute those costs among the business units using the services.
Enterprises can provide their internal Business Units with web access to
real time and historical charge back invoice information, as well as,
detailed IT usage reports.
- Budgeting and Planning. Enables enterprises to budget
and forecast IT costs based on collected historical IT usage data.
Business managers can view the variance between actual spending and
budgeted projections providing greater visibility into future IT cost.
Business managers gain the necessary information to accurately calculate
and justify future IT budgets to meet their future business objectives.
- End-to-End SLA
Management.
Ensures that service commitments are met and that appropriate levels of
service are provided, which meet business requirements. Service packages
suited to any business requirements can be created, and administrators
can define and implement SLAs and then track performance verses the
defined objectives. Service assurance can also be applied to monitor and
enforce service levels for third-party services. SLA
reports provide greater visibility into an enterprise's operation
environment, and overall health of IT resources from an IT administration
or end-user point of view.
- Service Catalog. Users can access and request service, as well
as review their account status. As an IT Administrator, you can track
user activity, set up accounts, review service reports, and set service
levels and rates for services provided. A service catalog also allows IT
to brand its services in order to better communicate the value that IT is
bringing to end-users and the enterprise.
- Unicenter Service Catalog
- Unicenter Service Catalog
serves as the gateway through which information is made available
anywhere via a Web Browser. Unicenter Service Catalog is also the access
gateway to other components in Unicenter Service Management.
- Unicenter Service Catalog lets
IT managers create a service catalog through which they easily can administer
and provide access to all their service offerings. Through the service
portal, users can quickly access their current services, browse
additional service offerings, subscribe to new services and review their
account status. Through the administrator view, IT managers can track
user activity, add and delete entries, review and publish service
reports, create new accounts and set service levels. By using the catalog
to define service parameters, managers can set technical and product
standards. Unicenter Service Catalog's simple Web interface is highly
customizable and displays can be viewed in multiple languages.
Administrators can view user activity by application, resource, Business
Unit, or any other defined organizational unit and can also brand service
offerings for specific groups of end-users.
- Unicenter Service Catalog
consists of the following
features:
Service catalog. Defines service offerings, captures
and maintains IT service components.
Organization structure. Defines an enterprise's organizational
structure, controlling access to and publishing information.
Web Based Service Portal. Acts as the gateway to information
collected by the Unicenter Service Management system complete with access
control settings, by role and business unit.
Scheduler. Schedules service management
associated tasks.
Reporting Engine. Has the ability to create tables
and charts with drill down capabilities from various data sources. Offline
reporting is also available and may be used to free up server resources.
Branding. Allows the product look and feel to
be customized by business unit and user without any coding.
Web Services Interface. Programmatic interfaces, allowing
quick and easy integration to other enterprise applications.
Pictured
below is a representation of the service catalog architecture. This depiction
demonstrates how an offering is comprised of rate plans, which in turn consist
of assorted rate items. These rate items in conjunction with there varying
associations constitute the inner workings of the service catalog:
- Offerings. A product, application, service, or simply something
you want to make available to your business units. An offering is then
associated with a rate plan, which contains the cost associated with subscribing
to it.
- Rate Plans. A rate plan contains the cost associated with
subscribing to an offering, based on transaction, usage based billing,
rate and more. It can be composed of many types of chargeable and
non-chargeable items, including applications, agreements, etc.
- SLA Package. A Service Level Agreement
(SLA) is a contract that specifies the level of service that will be
provided while the agreement is in effect. It is a bundling of service
level objectives for a particular enterprise resource. One of the main
components of an SLA package is an
application instance. You may define new SLA Packages through the Catalog
configuration definitions.
- Unicenter Service Catalog Portal is comprised of 2 components:
Content Library. The Portal Library, a directory of
published information where data is defined, organized and customized. This
data can be shared among users. Administrators can use role based and Business
Unit based access control to manage Content Library data. Users can publish
private data to the Content Library.
Presentation Dashboards. Used to view the information stored
in the Content Library. Personal Dashboards allow users to organize, integrate
and personalize data. Shared Dashboards are used to publish information to
users.
- Unicenter Service Fulfillment
- Using Unicenter Service
Fulfillment, an instance of a workflow process (also called a process
instance) can be launched through Rule Management in response to an
internal or external event or scheduled to be run on a regular basis using
the scheduler.
- Architecture. The Workflow architecture is shown below:

- Workflow Components. Unicenter Service Fulfillment consists of a
tool to define a business process model visually, various services for
executing the business process model, and a user interface for managing
and monitoring workflow processes and tasks.
Rule Management. Allows a Service Management
administrator to define an action or actions (in the form of scripts, Java
programs, E-mails, etc.) to be taken when a certain event is generated in
Unicenter Service Fulfillment Workflow Management.
Workflow Management. Allows a Service Management
administrator to monitor process instances executed by the Process engine. The
process engine is the core of the workflow management system, which executes
the process instances by following the flow in which they were defined. All the
rules and regulations that constitute a workflow process are resolved and
executed by the Workflow Engine.
Process Definition Tool. Sometimes referred to as the Workflow
IDE or Workflow Design Tool, this is your primary tool for maintaining process definitions, managing workflow
instances, and controlling workflow participant interaction.
Worklist. The Work list application lets you
manage tasks that are currently in your queue as well as the group's queue to
which you belong.
- Unicenter Service Meter is the
architecture designed to collect and normalize data into a common format,
preparing the data for business level applications, such as Unicenter
Service Accounting and Unicenter Service Assure. Unicenter Serv ice Meter
utilizes HTTP for data exchange, and is built on a lightweight, network
friendly and scalable push technology.
- Unicenter Service Meter
functionality includes:
Real-time
and batch data collection and aggregation
Monitoring
capabilities of dedicated or shared resources
Proven
methods of data collection
Data
integrity methods.
Self-deployment,
update and management of data collectors.
- Unicenter Service Meter
consist of the following features
Resource
tracking
Out-of-the-box
metering packages
Extendible
Resource Tracking Customizations
Data
Mediation
Failover
Mechanisms
Load-Balancing
Pre-build
metering reports
- Host Administration. An enterprise resource is classified as a Host
or Network Device. When creating a host through the Host Administration
GUI, the host type denotes whether the device is of type net device or
host. As an Administrator, you may add new hosts or drop hosts
- Metric Request. Ucenter Service Meter is responsible for data
collection. The metric request is a request to collect a particular
metric on a particular resource. It denotes the actual metric to be collected on a resource and the
data collection method used to collect metric data.
- Metric Diagnostic Reports. Diagnostic reports give
detailed information on every data collector and metric request. An
administrator can monitor data collection from a central location and
quickly pinpoint an error when an error in data collection occurs.
- Unicenter Service Assure
- With Unicenter Service Assure,
IT managers can monitor service levels from their user's point of view.
Known as end-to-end service-level reporting, the software allows them to
track an array of IT functions in aggregate. So, instead of reporting on
dropped CPU cycles, memory errors and network lag, they can demonstrate
the end result of all this activity in terms meaningful to their
end-users such as e-mail availability and response time.
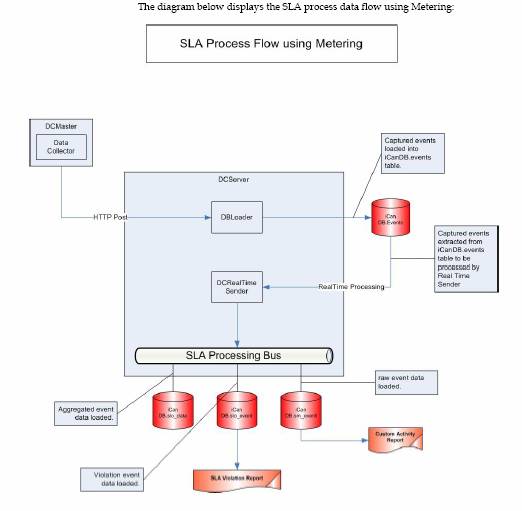
- Unicenter Service Assure Subcomponents. The Unicenter Service Assure
Engine runs as a Windows Service or a UNIX daemon and hosts four
sub-components. The components that can be installed during installation
are:
Processor. Monitors SLO's (Service Level
Objectives). The main SLO engine is designed to have multiple instances,
allowing you to split the workload across multiple machines. The workload
depends on the number of SLAs andSLOs you define in Unicenter Service Assure.
Database. Handles all database access. It can
be installed on a single machine that has the database drivers installed to
service the processors. Currently, the database component supports native
Oracle client, native Ingres client, or MSQL Server on the Windows platform.
Unicenter Service Management
Registry. Follows
the same philosophy as the database component.
Gateway. Provides a central access point to
allow external systems (for example Unicenter Service Meter) to send event data
to the processors. The gateway component is designed to have only one instance.
- Unicenter Service Accounting
- Unicenter Service Accounting
enables you to set up usage or transaction based billing through
Unicenter Service Meter, credit for violations through Unicenter Service
Assure, charge for subscriptions to the Catalog, and more.
- Uncenter Service Accounting generates
invoices based on real-time usage data and supports a variety of
chargeback methodologies.
- Unicenter Service Accounting
offers extended usage based chargeback over a wide range of supported
applications, networks, and applications, and other value added services,
including email transaction count by user, CPU usage on shared UNIX or
Windows servers by application , amount of storage used and allocated,
etc.
- Accounting Architecture
- Accounting Configuration. You may change the
configurations by clicking on the value and selecting a new value. The
Accounting Configuration window displays the following groups of fields:
Accounting
Profile Defaults
Invoice
Engine Configuration
System
Configuration
System
Configuration
Subscription
Configuration
Planning
Configuration
Payment
Methods
Invoice
Methods
Billing
Cycles







