|
|
|
Program: Remote Access over Network Projekt: RealVNC |
|
ZI5_Spajanje na RealVNC server_01.00.docDocument2 |
|
Zagreb, |
SPAJANJE NA RealVNC SERVER PREKO OpenSSHD SERVISA
OpenSSHD, Putty, WinSCP i RealVNC
|
Ratko Gospodnetić |
|
Radni dokument verzija: 01.00 |
Povijest dokumenta
|
Verzija |
Nadnevak |
Autor |
Status |
Napomena |
|
Ratko Gospodnetić |
radna verzija | |||
|
|
Zadnja pohrana:
SADRZAJ
UVODNE NAPOMENE
Sto je RealVNC
Sto je OpenSSHD
Sto je PUTTY
Sto je WinSCP
Instalacija programa RealVNC v4 Enterprise Edition
Instalacija programa OpenSSHD
Instalacija programa PUTTY
Instalacija programa WinSCP
Prilagodba Firewall zastite
Primjeri upotrebe RealVNC programa
POPIS TABLICA I SLIKA
Slika 1: Prijenos dokumenata i datoteka FTP protokolom
Slika 2: RealVNC omogućuje spajanje raznorodnih računalnih platforma
U redovnom radu (npr. konzultant u posjeti kod korisnika) često postoji potreba da se na priručno računalo (npr. Notebook) prenesu neki dokumenti ili datoteke s računalne mreze tvrtke.
Uz pretpostavku da je računalna mreza tvrtke spojena na Internet stalnom vezom (npr. stalna veza ili ADSL veza s dinamičkim DNS servisom) tada se prijenos dokumenata ili datoteke u oba smjera moze ostvariti uspostavljanjem FTP servisa na jednom od računala u mrezi tvrtke.
Primjenom odgovarajućeg FTP programskog servisa (npr. U-Serv) i odgovarajućeg programa na udaljenom računalu (npr. WS-FTP) moze se ostvariti veza uz pretpostavku da se na Firewall sustavu tvrtke dozvoli komunikacija na portu 21 (FTP-port).
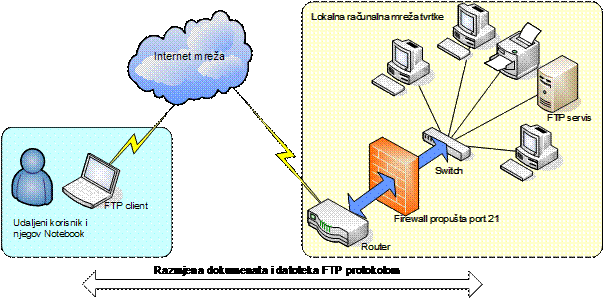
Slika : Prijenos dokumenata i datoteka FTP protokolom
Uz prijenos dokumenata i datoteka, FTP sustav treba omogućiti i upravljanje radom korisnika uz osiguranje privatnosti i zastite okoline i računala.
Ovakvo rjesenje zadovoljava zahtjev da se omogući prijenos dokumenata i datoteka u oba smjera, ali ne rjesava problem kad je potrebno iz bilo kojeg razloga na lokalnom računalu spojenom na računalnu mrezu tvrtke pristupiti s udaljenog računala spojenog na Internet te pokrenuti neki od lokalnih programa ili samo nadzirati njegov rad uvidom u zbivanja na ekranskom prikazu (Desktop
Za potrebe udaljenog pristupa na lokalnu računalnu mrezu te nadzor i upravljanje radom nekog računala treba na oba računala instalirati odgovarajuće računalne programa/servise te omogućiti njihovu komunikaciju kroz sustave zastite i Internet mrezu.
Posebni problem ovakvog rada je zastita sadrzaja prenesenih komunikacijskih paketa te zastita od neovlastenog pristupa na neko od računala lokalne računalne mreze tvrtke.
Na trzistu postoji niz proizvoda koji pokusavaju rijesiti ovaj problem te ponuditi podrsku za danas sve zahtjevnije i sve mobilnije korisnike.
Jedan od najstarijih i najpoznatijih proizvoda iz te klase je programski proizvod VNC (Virtual Network Computing) koji se uz besplatnu (Freeware) verziju sada nudi i kao komercijalni proizvod sa znatno unaprijeđenim svojstvima. Proizvod je promijenio ime i sada se zove RealVNC i nudi ga na trzistu tvrtka RealVNC[1] - vidi https://www.realvnc.com.
RealVNC je programski proizvod nastao iz programa VNC koji je u AT&T& laboratorijima u Cambridge, UK a bio razvijen kao pomagalo za spajanje računalnom podrzanih sustava.
RealVNC je opisan kao:
VNC stands for Virtual Network Computing. It is remote control software which allows you to view and interact with one computer (the "server") using a simple program (the "viewer") on another computer anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view an office Linux machine on your Windows PC at home. VNC is freely and publicly available and is in widespread active use by millions throughout industry, academia and privately.
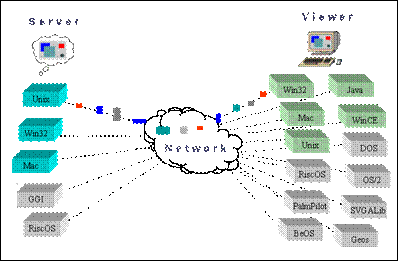
Slika : RealVNC omogućuje spajanje raznorodnih računalnih platforma
S obzirom da je TCP/IP najrasprostranjeniji komunikacijski protokol te da se njime moze ostvariti komunikacijska veza koristenjem Interneta, i RealVNC rabi za prijenos informacija taj protokol.
O sigurnosti RealVNC programskog sustava na njihovom informacijskom servisu pise:
Is VNC secure?
The only completely secure computer is one without a network. If a computer
does have a network connection, then it is only as secure as its weakest point,
whether this be the level of network encryption supported, the quality of
users' passwords, or the internal security of the server computer.
VNC Enterprise and Personal Editions include support for strong encryption and authentication of VNC connections. VNC Enterprise Edition additionally supports native authentication against system user accounts. Both versions are specifically designed to be used across untrusted networks such as the Internet.
VNC Free Edition and older VNC 3 based systems support a simple challenge-response protocol used to verify a password of up to eight characters, supplied by the connecting user. While this avoids exposing the password to attackers as would be the case with pure plaintext protocols such as telnet, the rest of the session is unencrypted and so anything typed into the viewer passes "in the clear" to the server. VNC Free Edition is therefore suitable for use within a local network or secure VPN, but not for general use over untrusted networks, such as the Internet.
Osnovu programske strukture čini VNC server koji se moze instalirati na mnogolike računalne platforme, te VNC preglednih (VNC Viewer) koji također uz Java verziju postoji za praktički sve postojeće računalne platforme.
RealVNC standardno rabi za komunikaciju port 5900 a za Java komunikaciju port 5800, pa treba osigurati da su na svim sustavima zastite na putu ostvarenja veze dozvoljeni i otvoreni komunikacijski kanali za te ili neke druge konfiguracijom odabrane portove.
Programski proizvod RealVNC raspoloziv je u nekoliko verzija:
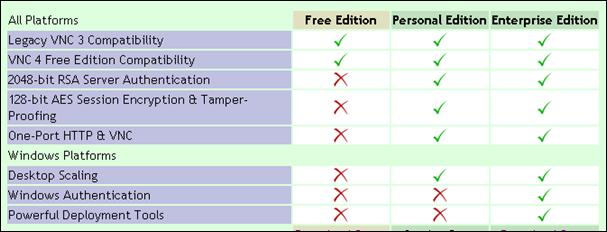
Slika : Usporedba verzija programskog proizvoda RealVNC
Iako RealVNC Enterprise verzija ima ugrađene mehanizme sigurnosti, razumno je osiguranje upotreba RealVNC sustava kroz stićeni tunel uspostavljen kroz SSH protokol.
How do I use VNC through my firewall?
Many organizations operate firewalls to reduce the risk of intrusion by
malicious attackers via the Internet. These firewalls typically operate by only
allowing connections in to machines in that organization on specific ports.
Which ports are permitted access depends upon the network protocol that uses
the port and the degree of security it provides.
There are two main methods for making VNC servers accessible through firewalls:
Opening Ports - If you are using a secure version of VNC, such as VNC Enterprise Edition, you can simply configure your firewall to permit traffic on the port(s) used by the server. If your VNC server is configured to accept connections on VNC Display Number N (equivalent to Port Number 5900+N), then port 5900+N must be configured to be allowed through the firewall. To allow the Java VNC Viewer to be served through the firewall, port 5800+ must also be allowed through, or you must configure your VNC server to use the same port for both the VNC and Java Viewer connections, if possible.
Secure Tunneling - Most organizations that operate firewalls allow connections to a number of standard ports, which are in principle used only by secure or harmless protocols. The Secure Shell (SSH) protocol, for example, acts as a wrapper around other protocols, allowing them to be used securely over the Internet, and is a protocol which most firewalls allow access through. A Secure Shell client is run on the VNC Viewer computer and is made to forward connections to a particular port on that machine to a port on the VNC Server machine. The forwarded connection is encrypted by the SSH software, which can provide both encryption and authentication.
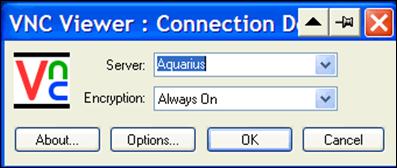
Slika 4: VNCviewer - Prijava na VNC server
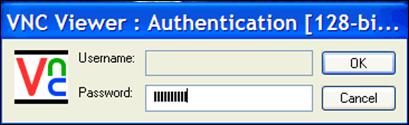
Slika 5: VNCviewer - upis zaporke (Password
Slika : VNCviewer - ekranski prikaz računala na kojem je instaliran VNC server
Kako je TCP/IP nedovoljno siguran protokol i nije adekvatno stićen, potrebno je ostvariti komunikacijski mehanizam u kojem će se zbivati prijenos informacija sa i na računala uz maksimalnu sigurnost podataka. Takav mehanizam pruza primjena SSH protokola koji moze ostvariti "tunelsku" sigurnu vezu između dva računala, a unutar kojeg se mogu odvijati drugi komunikacijski procesi zastićeni sigurnosnim slojem SSH (SSH = Security Shell) prijenosa.
SSH protokol je definiran kao:
About SSH
SSH is a secure way to connect to another computer system. This protocol supports a telnet alternative (usually called SSH itself), a secure file copy program (SCP) and a secure FTP program (SFTP or WinSCP[2]). The SSH protocol also lets you establish secure connections with other programs or protocols through the use of port forwarding. This means that mail protocols, VNC, and other programs can be used with encryption between two machines.
Secure Shell (SSH), sometimes known as Secure Socket Shell, is a UNIX-based command interface and protocol for securely getting access to a remote computer. It is widely used by network administrators to control Web and other kinds of servers remotely. SSH is actually a suite of three utilities - slogin, ssh, and scp - that are secure versions of the earlier UNIX utilities, rlogin, rsh, and rcp. SSH commands are encrypted and secure in several ways. Both ends of the client/server connection are authenticated using a digital certificate, and passwords are protected by being encrypted. SSH uses RSA public key cryptography for both connection and authentication. Encryption algorithms include Blowfish, DES, and IDEA. IDEA is the default.
SSH is a protocol that allows you to encrypt all data traveling from your computer to your server or other computer using different types of encryption algorithms. The server you are connecting to must be running SSH, and you must be running a secure shell client on your own machine as well.
SSH normally just provides you with a 'Secure SHell' - i.e. a login window to a remote machine. All traffic is encrypted between the two machines using public key encryption techniques, making it really very difficult for anyone else to spy on it. Once SSH is installed, you could connect to a machine called 'snoopy' from elsewhere simply by running the SSH client
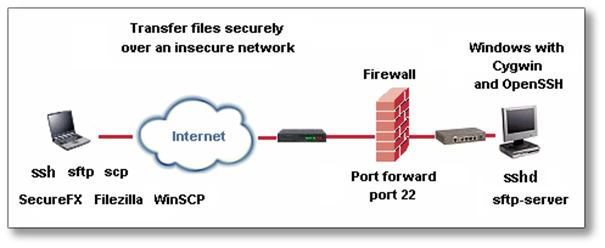
Slika 7: SSH prijenosni put
About OpenSSH
From the
OpenSSH Project History Page:
OpenSSH is a derivative of the original free ssh 1.2.12 release from Tatu
Ylönen. This version was the last one which was free enough for reuse by our
project. Parts of OpenSSH still bear Tatu's license which was contained in that
release. This version, and earlier ones, used mathematical functions from the
libgmp library. That library was also included with these early ssh versions.
The libgmp library is made available under the (LGPL) Lesser GNU Public
Licence, although versions of that era were under the regular (GPL) GNU Public
Licence.
About the OpenSSH for Windows Package
The OpenSSH for Windows package is a repackaging of the OpenSSH port to the Cygwin environment. While not a native Windows port, this goal of this distribution has been to run the OpenSSH client and server programs with as little of the Cygwin environment as possible. This helps Windows administrators who might be unfamiliar with the Unix environment and helps users with access to the Windows command line interface. As with the OpenSSH and Cygwin packages, this software is also being distributed free to any user who is looking for a more secure way to remotely administer their Windows machines
Tested Configurations
Microsoft has a lot of Windows configurations (Counting releases since Windows NT 4.0, there are over 10!). I really cannot test all configurations possible on all of these releases. Following is a list of the configurations I have tested my OpenSSH for Windows with. All tests were conducted with default NTFS permissions. Users who change their default security configurations will have to sort out things if the package does not work.
Tested with:
Windows NT 4.0 Workstation with SP6a
Windows 2000 Professional with SP3
Windows 2000 Server with SP3
Windows XP Professional
Windows 2003 Server, Enterprise Edition
OpenSSH for Windows
OpenSSH for Windows is a free package that installs a minimal OpenSSH server and client utilities in the Cygwin package without needing the full Cygwin installation. This is similar to the package formerly available from NetworkSimplicity.
The OpenSSH for Windows package provides full SSH/SCP/SFTP support. SSH terminal support provides a familiar Windows Command prompt, while retaining Unix/Cygwin-style paths for SCP and SFTP.
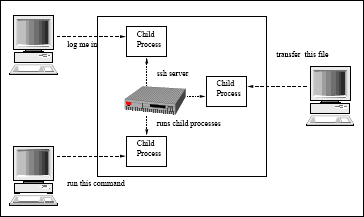
Slika 8: SSH temeljni koncept arhitekture
SSH has a client/server architecture.. An SSH server program, typically installed and run by a system administrator, accepts or rejects incoming connections to its host computer. Users then run SSH client programs, typically on other computers, to make requests of the SSH server, such as "Please log me in," "Please send me a file," or "Please execute this command." All communications between clients and servers are securely encrypted and protected from modification.
Although SSH stands for Secure Shell, it is not a true shell in the sense of the Unix Bourne shell and C shell. It is not a command interpreter, nor does it provide wildcard expansion, command history, and so forth. Rather, SSH creates a channel for running a shell on a remote computer, in the manner of the Unix rsh command, but with end-to-end encryption between the local and remote computer.
SSH is also not a complete security solution -- but then, nothing is. It won't protect computers from active break-in attempts or denial-of-service attacks, and it won't eliminate other hazards such as viruses, Trojan horses, and coffee spills. It does, however, provide robust and user-friendly encryption and authentication
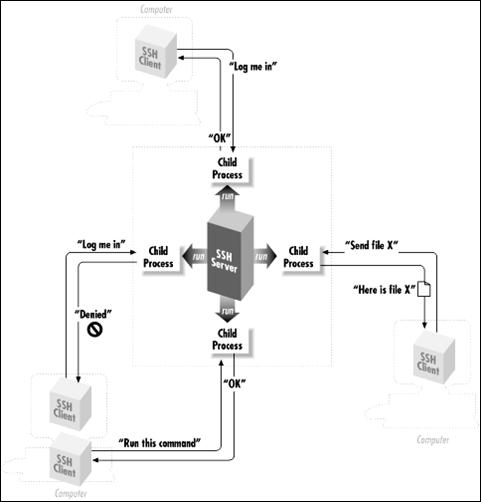
Slika 9: SSH generička arhitektura
The SSH Protocol
SSH is a protocol, not a product. It is a specification of how to conduct secure communication over a network.
Although we say "the SSH protocol," there are actually two incompatible versions of the protocols in common use: SSH-1 (a.k.a SSH-1.5) and SSH-2.
The SSH protocol covers authentication, encryption, and the integrity of data transmitted over a network, Let's define these terms:
Authentication
Reliably determines someone's identity. If you try to log into an account on a remote computer, SSH asks for digital proof of your identity. If you pass the test, you may log in; otherwise SSH rejects the connection.
Encryption
Scrambles data so it is unintelligible except to the intended recipients. This protects your data as it passes over the network.
Integrity
Guarantees the data traveling over the network arrives unaltered. If a third party captures and modifies your data in transit, SSH detects this fact
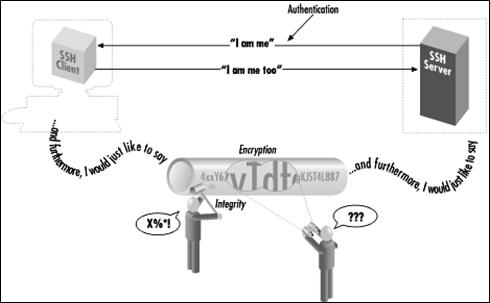
Slika : Authentication & Encryption & Integrity
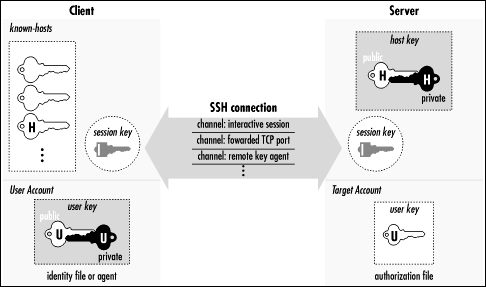
Slika 11: Razmjena kriptografskih ključeva između servera i clienta
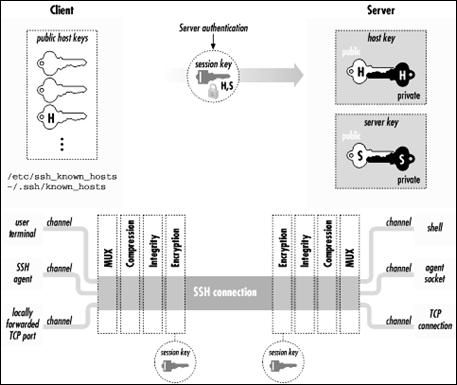
Slika 12: Arhitektura SSH-1 protokola
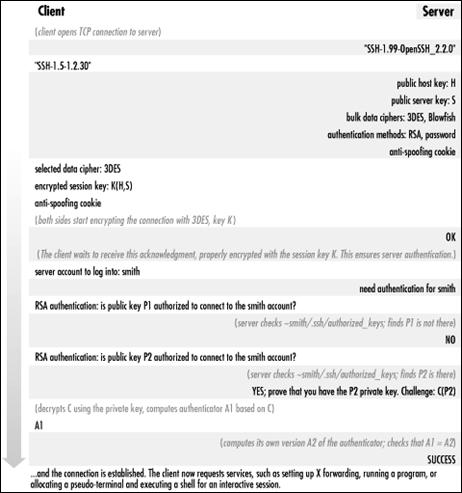
Slika 13: SSH-1 protokol - razmjena podataka između clienta i servera
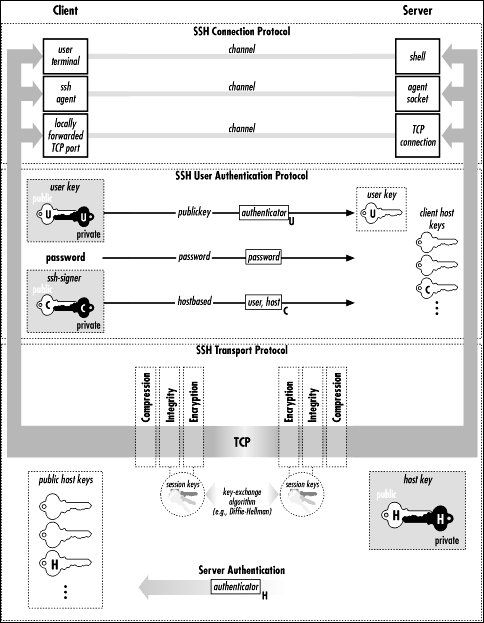
Slika 14: Arhitektura SSH-2 protokola
Usporedba SSH-2 i SSH-1 protokola
|
SSH-2 |
SSH-1 |
|
Separate transport, authentication, and connection protocols. |
One monolithic protocol. |
|
Strong cryptographic integrity check. |
Weak CRC-32 integrity check. |
|
Supports password changing. |
N/A |
|
Any number of session channels per connection (including none). |
Exactly one session channel per connection (requires issuing a remote command even when you don't want one). |
|
Full negotiation of modular cryptographic and compression algorithms, including bulk encryption, MAC, and public-key. |
Negotiates only the bulk cipher; all others are fixed. |
|
Encryption, MAC, and compression are negotiated separately for each direction, with independent keys. |
The same algorithms and keys are used in both directions (although RC4 uses separate keys, since the algorithm's design demands that keys not be reused). |
|
Extensible algorithm/protocol naming scheme allows local extensions while preserving interoperability. |
Fixed encoding precludes interoperable additions. |
|
User authentication methods: public-key (DSA, RSA, OpenPGP) hostbased password (Rhosts dropped due to insecurity) |
Supports a wider variety: public-key (RSA only) RhostsRSA password Rhosts (rsh-style) TIS Kerberos |
|
Use of Diffie-Hellman key agreement removes the need for a server key. |
Server key used for forward secrecy on the session key. |
|
Supports public-key certificates. |
N/A |
|
User authentication exchange is more flexible and allows requiring multiple forms of authentication for access. |
Allows exactly one form of authentication per session. |
|
Hostbased authentication is in principle independent of client network address, and so can work with proxying, mobile clients, etc. |
RhostsRSA authentication is effectively tied to the client host address, limiting its usefulness. |
|
Periodic replacement of session keys. |
N/A |
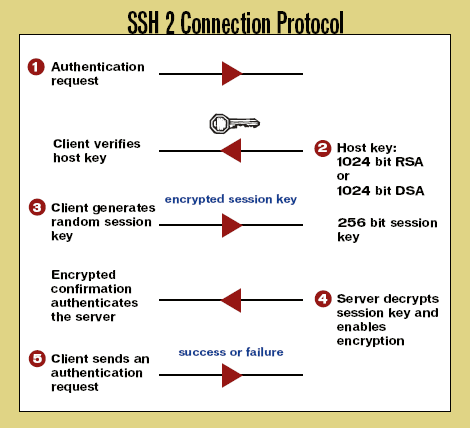
Slika 15: SSH-2 protokol uspostavljanja veze
Terminology: SSH Protocols and Products
SSH
A generic term referring to SSH protocols or software products.
SSH-1
The SSH protocol, Version 1. This protocol went through several revisions, of which 1.3 and 1.5 are the best known, and we will write SSH-1.3 and SSH-1.5 should the distinction be necessary.
SSH-2
The SSH protocol, Version 2, as defined by several draft standards documents of the IETF SECSH working group.
SSH1
Tatu Ylönen's software implementing the SSH-1 protocol; the original SSH. Now distributed and maintained (minimally) by SSH Communications Security, Inc.
SSH2
The "SSH Secure Shell" product from SSH Communications Security, Inc. (https://www.ssh.com). This is a commercial SSH-2 protocol implementation, though it is licensed free of charge in some circumstances.
ssh (all lowercase letters)
A client program included in SSH1, SSH2, OpenSSH, F-Secure SSH, and other products, for running secure terminal sessions and remote commands. In SSH1 and SSH2, it is also named ssh1 or ssh2, respectively.
OpenSSH
The product OpenSSH from the OpenBSD project (see https://www.openssh.com/), which implements both the SSH-1 and SSH-2 protocols.
OpenSSH/1
OpenSSH, referring specifically to its behavior when using the SSH-1 protocol.
OpenSSH/2
OpenSSH, referring specifically to its behavior when using the SSH-2 protocol.
What is PuTTY
PuTTY is a free implementation of Telnet and SSH for Win32 and
Unix platforms, along with an xterm terminal
emulator. It is written and maintained primarily by Simon Tatham.
PuTTY is a client program for the SSH, Telnet and Rlogin network protocols.
These protocols are all used to run a remote session on a computer, over a network. PuTTY implements the client end of that session: the end at which the session is displayed, rather than the end at which it runs.
In really simple terms: you run PuTTY on a Windows machine, and tell it to connect to (for example) a Unix machine. PuTTY opens a window. Then, anything you type into that window is sent straight to the Unix machine, and everything the Unix machine sends back is displayed in the window. So you can work on the Unix machine as if you were sitting at its console, while actually sitting somewhere else.
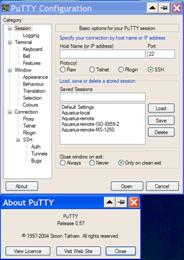
Slika : PuTTY Startup & Configuration ekran
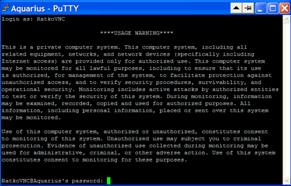
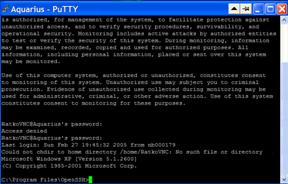
Slika 17: PuTTY Login ekran prije i nakon uspjesno upisane zaporke (Password
Introducing WinSCP
WinSCP is an open source freeware SFTP client for Windows using SSH. Legacy SCP protocol is also supported. Its main function is safe copying of files between a local and a remote computer.
WinSCP can do all basic operations with files, such as copying and moving (to and from a remote computer). It also allows you to rename files and folders, create new folders, change properties of files and folders, and creating symbolic links and shortcuts.
One of two selectable program interfaces (based on Norton Commander) allows the user to manage files even on the local computer.
Most operations can be done recursively for files in folders. In some cases optionally (changing of file properties), in all other cases it's compulsory (copying, moving, deleting).
Graphical user interface
Translated into several languages
Integration with Windows (drag & drop, URL, shortcut icons)
All common operations with files
Support for SFTP and SCP protocols over SSH1 and SSH2
Batch file scripting and command-line interface
Integrated text editor
Support for SSH password, keyboard-interactive, public key and Kerberos (GSS) authentication.
Integrates with Pageant (Putty Agent) for full support of public key authentication
Windows Explorer-like and Norton Commander-like interfaces.
Optionally stores session information.
Optionally supports standalone operation using a configuration file in place of registry entries, suitable for operation from removable media
Directory Synchronization tool quickly synchronizes changes between local and remote directories.
Changing User Interfaces
During installation, you will have the first chance to select your preferred user interface. You may want to change your preferences later. One of the ways is on Preferences page on Login dialog.
The first one is based on Norton Commander (and similar file managers). A local folder is displayed in the left panel and a remote folder in the right panel. Files are usually transferred between these two folders, though it is possible to transfer files into a different folder.
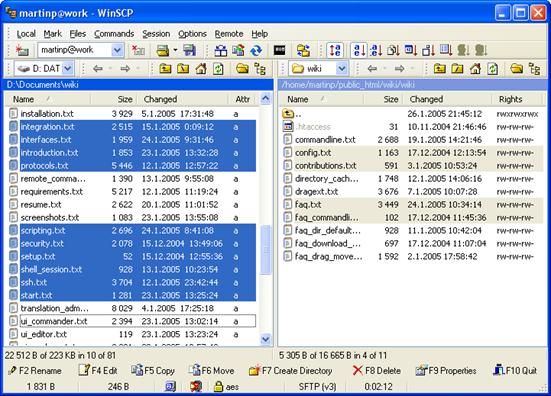
Slika 18: WinSCP - Norton Commander sučelje
Explorer-like Interface
The second interface is similar to Windows Explorer. Only the remote folder is shown. Files are transferred by typing the target local directory or by Drag & Drop. This method is provided in both interfaces.
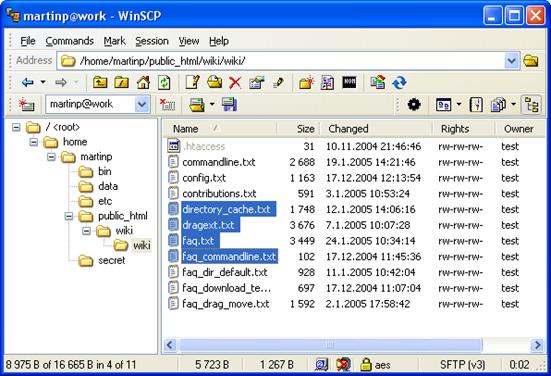
Choosing the Right User Interface
If you are using WinSCP for the first time, you may wish to select the Explorer-like interface as it should be familiar to any Windows user. However if you are used to the concept of Norton Commander, used by several contemporary file managers (Total Commander, FAR, Servant Salamander), choose this one. Norton commander interface is primarily focused on easy keyboard control. You can use it without ever touching mouse. One who is used to it can perform the operations much faster.
Da bi se mogla ostvariti sigurna komunikacija zasnovana na javno raspolozivim programskim proizvodima potrebno je:
Ako ne postoji potreba za visokom sigurnosti ili ako postoji na raspolaganju VNC programski proizvod koji sam po sebi ima visoku razinu zastite i enkripcije (kakav je npr. RealVNC v4 Enterprise Edition) tada se ne mora instalirati SSH servis na serveru, ali tada treba na sigurnosnoj brani (Firewall) otvoriti konfigurirani port (za VNC je pretpostavljeno da radi na portu 5900).
Ako se zeli koristiti Java VNCviewer tada treba biti ili otvoren port 5800 ili ga treba prekonfigurirati na 5900 kao i osnovni port za VNC komunikaciju.
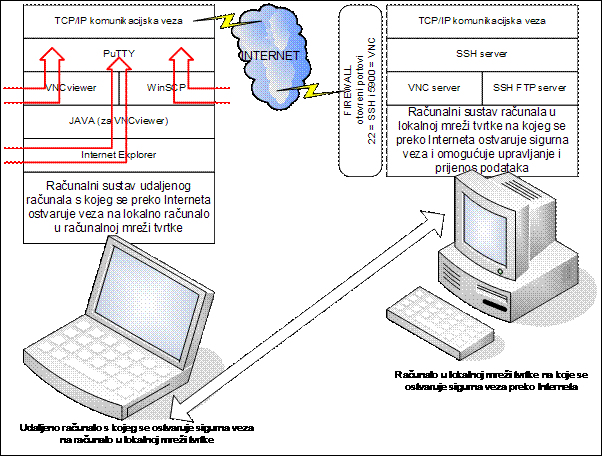
Slika 19: Opći princip povezivanja i primijenjeni programski alati
|